leftychan.i2p
Hello, faggots, thanks to our unwavering dedication to the community I am proud to announce we are rolling out our own, official, leftychan.net i2p address.You can locate the eepsite @ http://leftychmxz3wczbd4add4atspbqevzrtwf2sjobm3waqosy2dbua.b32.i2p, or, http://leftychan.i2p/.
If you have any trouble, as stated on the news announcement, try manually adding the address and domain to your address book.
-Yours Truly.

/ttg/ - Tech Team General
This thread is only for feedback related to technical issues(bug reports, suggestions). Otherwise use >>>/meta/10032Public Repo: https://github.com/towards-a-new-leftypol/leftypol_lainchan
If you have any grievances you can make a PR.
Mobile Support: https://github.com/PietroCarrara/Clover/releases/latest
Thread For Mobile Feedback: >>>/tech/6316
Onion Link: http://leftychans5gstl4zee2ecopkv6qvzsrbikwxnejpylwcho2yvh4owad.onion
Cytube: https://tv.leftychan.net
Matrix: https://matrix.to/#/#Leftypol:matrix.org
Once you enter, consider joining the lefty technology room.
We are currently working on improvements to the site, subject to the need of the tech team to sleep and go to their day jobs. If you need more immediate feedback please join the matrix room[s] and ask around. Feel free to leave comments, concerns, and suggestions about the tech side of the site here and we will try to get to it as soon as possible
Archived thread:
>>>/leftypol_archive/903

A moment to talk about Anon networks and its current state
Can we please Have a moment and talk about the current state of anonymization networks, and how to best fix it for anymetadata and leaks? What to tweak to make it more secure
As we all know TOR is glowing, created and funded by them. Maintained and directory nodes being owned by them, and probably
a majority of nodes. I thought I2p would be better so i just got into it. And started reading about its problems, and beef with devs.
Found following posts on some chans, and wanted some other peoples opinion..
So is it all always glowing? cant we have a network actually made by people for people?
——-
https://paste.coalserver.de/?5eb32f413de27fab#6QdH6kVtsR81E4tcXDfDkp13XQbFWNzsFkyqVx9TF9HE
0x0.st/PZOy.txt
also what r the problems with networks like Lokinet, freenet, gnunet and yggradsil? except for the cheese pizza(tbh aint that hosted
by glowies themselves?)
So for TOR the securest way would be some laptop with libreboot, qubes and whonix. And for i2p/i2pd just changing your b32 adresses
and using new tunnels for every connection? what about the router id? that stays even after a reboot?
And how much of a pro is using a VPN paid with XMR before connecting to i2p and tor? its either the ISP sees the traffic,
or someone providing the proxys. I didnt fully get the part with i2p routers and ip adress correlation, but wouldnt a proxy solve that?
Also apparently, very poor information about how to correctly run i2p, being a floodfill router exposes your home IP and router ID
to the netDB to connect to other routers and support the network, the router ID being connected to the b32 adresses that the eepsites see.
So someone scraping netDB for floodfill routers, would be able to connect the routerID with the b32 adresses. and ur IP then.
whats this bullshit?
Also where else could i post this? lamdaplus /tech/ seems kinda active 4chan doesnt allow proxies.
any other spaces that are active?

Less retarded software
I made a wiki about unretarding technology and society. What do you think? https://www.tastyfish.cz/lrs/main.html
Signal Jamming
Picture this:>Armed citizens surround ICE as they're arresting someone
>ICE calls for backup
>Nobody hears them
>They have no choice but to let the person go
I'm assuming they are using off-the-shelf radio equipment.
Is it easy to jam their signal with portable equipment?
How hard/expensive is it to build a DIY radio jammer?
Would it be more effective to have a directional antenna to avoid jamming everything in the area and concentrate on one area, or it doesn't work that way?

A proper FOSS messenger, alternative to Discord.
Hello people. I'm looking for an instant messenger which satisfies most of those needs:Anonymous, private & secure [decentralised, encrypted & safe] (Hard necessary)
Audio & video calls [configure volume, deafen, mute, select camera/screen/window & support for group chats] (If there is an app which satisfies most other needs but does not have audio/video, I might do fine just using Jitsi instead, so it's mid-necessary.)
Clean, fast, professional, responsive & smooth design (Can also go with terminal)
Cross-platform [android, linux & windows] (Hard necessary)
File transfer [no limits] (Hard necessary)
Free & open source (Hard necessary)
Group chats [customisation & moderation] (Hard necessary)
History [clear, search system] (Favorable, but not necessary)
Notifications [togglable] (Favorable, but not necessary)
Presence [do not disturb, online, idle] (Favorable, but not necessary)
Stable & optimised [performant & lightweight] (Hard necessary)
Status [media & text] (Favorable, but not necessary)
Folders [contacts & groups] (Favorable, but not necessary)
Text messaging [block, delete, edit, embed, emoji, format, mark as unread, mention, mute, show typing, pin message/user, quote, react, read receipts, reply, saved messages, spell checker, etcetera] (Not all those features listed are hard necessary)
I'm just looking for an alternative to fbi.gov, there has to be no ZOG crap, that's the first need listed.
I found this abandoned repository https://gitgud.io/parley/Haruko.
It's imageboard software that's not that old but still works. This is what it looked like: https://archive.is/qiLyz.
and I would like your help in updating it. It would be a project for “new” imageboard software made with PHP because, from what I've seen, there aren't many like this left, so I created this repository: https://github.com/bigdustycheese/AobaIB which I will update and you will also help me with.
>>Why should we help you with this? What do I get in return, OP?
It's simply a collaborative fork. If you want to help me, that's fine. No one is forcing you.
(If you see this on other imageboards, it's not spam.)

Image Format Wars
So apparently Palemoon became the first browser to officially implemented JPEG XL a week ago. At the same time, Google just dropped it from Chromium despite supporting it behind a flag for months. What the hell is going on here? Is Google that desperate to push their video-codecs-as-image-formats that they're willing to sabotage a massive step forward for the web? JPEG XL is capable of replacing both original JPEG, PNG, and animated GIF/PNG all at once with a single file type that produces superior file sizes for all three categories of use cases. Neither WebP, HEIC, nor AVIF were ever able to make such a broad, sweeping improvement because they are geared more towards features important to video encoding than still images or lossless animation.It seems like every few weeks these days I find something new to get mad about in the world of web development.

Chinese breakthrough in nuclear power
So it seems that after decades of neglect and sabotage by the cuclear weapons industry, China has successfully built a fully functional molten salt thorium reactor and is preparing to revolutionize global shipping by sticking it in cargo ships.https://interestingengineering.com/transportation/thorium-powered-nuclear-cargo-ship
They've even appl the supercritical CO2 generator idea that was a nascent engineering concept by Western thorium power advocates. This could have applications even beyond nuclear power generation.

drm-web ai-web
Google wants to put DRM into the web, and lock everything into their chrome browser and make privacy violations even worse.I think this is part of bigG's war on addblocking and of course they're a monopoly that wants to be the entire web. But there is more, web-advertising has been sort of dying a slow death for some time now. Not because of addblock but for other reasons. Neo-liberalism/capitalism is making people poor and that's shrinking the economic pie in general. If people see adds they ignore them more often. And there is of course the scheme for generating fake views for add-farming.
The drm googl wants to insert into the web is super terrible, if they can push this through it will destroy the web. There is no hyperbole here, the web will become like one of those locked down alternate versions of the internet from the 80s that failed so hard that barely anybody remembers that they even existed. It's possible that EU regulations against anti-competitive behavior, and monopoly-busting in the US could cock-block google, but it would be better to fight tooth and nail to kill this one in the crib, before it gets anywhere near that point. And then outlaw DRM for violating personal property (if you can't fully control your gadgets you've been expropriated)
If this monstrosity were to happen, it would probably take over 10 years to polish one of those decentralized peer to peer alternative web-protocols to the point where we get something like an open web back.
For more details see
The Linux Experiment
https://invidious.0011.lt/watch?v=Aj2s3DVSlHw
https://www.youtube.com/watch?v=Aj2s3DVSlHw
Brodie Robertson
https://invidious.0011.lt/watch?v=tm3gH-ycykw
https://www.youtube.com/watch?v=tm3gH-ycykw
Louis Rossmann
https://invidious.0011.lt/watch?v=0i0Ho-x7s_U
https://www.youtube.com/watch?v=0i0Ho-x7s_U
Web Environment Integrity API Proposal
https://news.ycombinator.com/item?id=36817305
This is probably somewhat related to the AI-web eating the web2.0 by scraping all it's content without generating any add-views/revenue.
The solution to this however is not drm-ing the web to death, but rather replacing the web2.0 web-page front-end interface with an AI interface. That way you can't just scrape an entire website. You're scrape-bot would have to send a bazillion queries to the AI interface. And the AI interface could of course be trained to tell scraping behavior from a normal human interaction and feed the scrape-bot a bunch of "AI-hallucinated" nonsense.
The AI interface would be trained on the content in the database of a website, and converse about a narrow range of topics based on the knowledge that you put into the back-end database. Of course there could be AI-adverts, in the form of the AI trying to work product suggestions into the conversations with users.
A key for making this economically viable is that a bunch of the processing for ai-pages is done on end-user hardware, which would need Machine-Learning Accelerator hardware, to be efficient and fast. Arm-socs for phones had this for a while, x86 desktop processors are somewhat behind on this and only the latest AMD processor already have dedicated MCA-cores. (dedicated gpu-pcie cards can do this too).
I'm not saying ai-adds should be the business model for this. Consider the add-revenue from a single page-view is a tiny fraction of a cent. If users could pay a fix sum of money into a pot and that gets distributed according to user page views, in a privacy respecting way, websites could make money without adds. I'm guessing here but if the average user were to spend 20 bucks a year, website operators would probably get more money than they do now with add-sense and co. Consider this proposal in the context of being limited by capitalism being utter dogshit in producing economic relations that work well with high-tech.
This AI-web would kill traditional web-crawlers/spiderbots (the thing that search engines use to index the web and give you search results). A new method of indexing AI-pages would need to be devised. This would probably be a technical problem google could solve, but they appear to be going into the polar-opposite direction.

Downloading youtube
I'm tryna download this video https://www.youtube.com/watch?v=BVlfNtIml2U and yt-dlp gives me a 403 error
wat do

Google Antitrust
https://archive.is/Qt0n1So it seems a US court has just ruled that Google monopolized the online search market. Now the Department of Justice is "considering" breaking up Google as a potential option in response.
At long last is there finally some hope for the future of the web?

Cloudflare is malicious software
For an entire month now, Cloudflare has been discriminating against alternative web browsers to the Google hegemony by refusing to "verify" them as legitimate browsers through their browser check loop. On some browsers this has been blatantly malicious by designing the loop to hang indefinitely while it rapidly consumes all of the user's memory until a program crash. This has included Palemoon, Librewolf, Waterfox, IceCat, Seamonkey, Falkon, and more. Basically it seems like anything that isn't a subservient Chrome fork or Firefox itself is being gatekept out of the web by Cloudflare. The likelihood that this is being done deliberately is high because a) they have been doing it for an entire month, b) the entire time they have refused to respond to developers reaching out asking them to fix it, and c) Cloudflare themselves have stated that their secret proprietary methods of fingerprinting "human" browsers are tailor-fit to each browser. Some links following this story:https://forum.palemoon.org/viewtopic.php?f=3&t=32045
https://news.ycombinator.com/item?id=42953508
https://soylentnews.org/article.pl?sid=25/02/07/044225
http://techrights.org/n/2025/02/20/Instead_of_DoS_Protection_Cloudflare_is_Allegedly_Conducting_Do.shtml
In only the span of a few years, DDoS "protection" services have grown to exert so much control over the web that they can now play kingmakers in browser competition and coerce user choice. We need a solution to the DDoS protection racket more than ever. What can be done about this?

holographic communication
In the early 20th century armies used search lights to find airplanes in the sky. They sometimes fitted shutters on these lights and used them for Morse-code. The light was pointed at the sky, sometimes at clouds. That enable transmitting "blinky-messages" beyond line of sight over significant distances. Armies eventually abandoned this method of communication for radios.But there might be cause to bring this idea back. Science has advanced quite a lot in the last 100 years and we can use light to make tiny low power plasma bubbles in the air that emit brief light pulses. Enabling over the horizon optical communication with minimal to no infrastructure costs.
Imagine projecting a tiny holographic blinking dot of light in the sky to transmit information and a photodetector+optic to receive information.
A communication link is configured in 3D space.
-The upside is that the available volume of sky is functionally unlimited, and you never again have to deal with network-collisions and interference from communication signals of others.
-The Downside, it requires a good deal of precision in mechanical systems, so it'll be fiddly for a while. Picture using Binoculars to look at a firefly floating high up in the sky, you need to get up-down, left-right and focal distance just right to see it. There is a technology upgrade path to a solid-state chip version, that works similarly to matrix array antennas, It needs Terra-hertz switching logic, which requires photon-based micro-controller (it exists but it's very bleeding edge)
The range can be tremendous, there is enough gas molecules in the stratosphere to make this work. It will enable hops over the ocean with a small number of relay buoys.
The military might want this technology because
- it's harder to triangulate the origin of a transmission (you need to intersect the light-beam, to find the source), relay-transmitter-stations, soldiers, planes and ships will suffer fewer attacks from signal homing weapons, making it very robust.
- it's very hard to jam, (you need to flood the sky with very thick smoke, usually associated with forest-fires and volcano eruptions)
Consumers might want this technology because
- the patent for making plasma bubbles ran out, so lots of companies would be competing on price and quality.
- no natural monopolies, same benefit as above.
- might be a fun hobby toy for radio-enthusiast type people.
Technically this seems very feasible, but the current political climate for communications-tech is a minefield.
I'm a little light on theory, will a different communication technology change the political climate, or does political climate need to improve to make a new technology happen ?

I don't know about you, but 4chan has long needed peace; it has not been anonymous for a long time, it uses a captcha that collects user data, and if it blocks users, that's just life. Where is your anonymity? Reddit, at least, allows you to create an account with a proxy or VPN. And what is 4chan? There is also a Russian-speaking equivalent called Dvach, which is even worse; it even blocks posts that are not from Russia. What kind of nonsense is that? There is also a law prohibiting GPT, and God forbid you joke about politicians; they will simply ask the owner of Dvach to leak your IP, and that's it. So the only anonymity is the absence of identification, but for the provider, you are still the same. In short, these sites are dead. In short, I have long been waiting for your opinions and criticism; if I am mistaken or wrong about something, please let me know.

Radlibs are trying to cancel FSF and Stallman
I know I am a little bit late to the party with this but some "anonymous" group tried to cancel rms and the FSF as well: archive.md/Pt37W (stallman-report.org). It's the usual shit: whining about Stallman's comments on Epstein, supposed "sexual harassment" etc. Basically, the author calls for Stallman to step down from the FSF and/or for FSF members to take him down.It is already known who wrote this "report": Drew DeVault, a developer who worked (or still works?) on Wayland. https://news.ycombinator.com/item?id=41859793

Is protonmail a honeypot?
>Trying to sign up on .onion links back to .com
>Can't sign up with vpn
>Only accepts crypto after you've signed up
There's absolutely no reason for not allowing sign-ups with vpns/TOR and activating the accounts after the payment has gone through
Do there exist any alternatives that aren't glowies?

My thoughts on AI
I believe both sides can be quite extreme so here's my balanced take:>supplementary use of AI (chatbots, TTS, NPCs, enemy AI, RPGs, level generation, self-driving cars, AI assistants and code generation) are pretty based actually as long as they produce correct outputs and don't get you into any legal trouble
>non-commercial use of AI is also fine and can create something unique and interesting (memes, AI covers, AI dubbing)
>AI art is mostly slop except for some rare exceptions so people should at least be able to easily filter it and it should be marked appropriately
>commercial use of AI other than what was already mentioned is NOT cool and leads to more layoffs, more enshittification, more plagiarism and more mass surveillance
>proprietary AI software is ALSO not cool since it can be spyware that sends your data to the NSA

Bizarre accessories
Post bizarre/amuzing device accessories you found.https://www.theverge.com/news/638284/dbrand-touch-grass-skin-tablet-smartphone-handheld-console
<April Fools’ 2025: Dbrand’s new skins let you ‘touch grass’ without the hassle of going outside
dbrand just committed WatchMojo and redeemed itself in my eyes.

Why just about nobody seems to care about risk of strong solar storm on the scale of the carrington event?
Why there are no procedures made, spare transformers produced, emergency food and supplies stored around major cities, etc?
People care about climate change risks slowly damaging civilization over decades, and here we have risk (also scientifically and historically proven) that can just randomly disable worldwide electricity next year (extremely unlikely) or during the next 200 years (LIKELY) and we are doing nothing?
What is the logic in this? "Unlike climate change it will happen randomly, it may happen in 2054 or 2077, we may be already dead, we don't care"?
(No, nobody said that, I'm just trying to imagine reasons needed to ignore the issue).
Do you care about people who are now small children?
"It will PROBABLY not happen during my remaining lifetime, I'm fine with only 10% risk of dying from hunger or disorder among collapsing civilization"?
What is the logic here? What is the plan?
Are the risk overblown?
Or is the total fall of the industrial civilization so utterly and completely sure that there is no value of trying to save anything at all? Maybe at least some sort of archives carved on f****g stone, if not spare transformers, comms in Faraday cages and parts. Christ.
Or perhaps nobody outside of 20 scholars and Wikipedia heard about this issue?
Topic just unknown/boring (LOL) even for influential staff at FEMA?

nintendont
A video game that nintendo had a legal distribution monopoly on was leaked ahead of the official release. They got really mad about that and they are trying to take it out on the video-game emulation communities, by attacking emulation related software projects on github.So the lesson here is if you give companies like that money they are going to use it to attack your hobbies. I think this legitimizes "pirating" games because you have no legal option to buy these games without also supporting nintendo's legalistic mafia-terror.
If copy"right" wasn't set up like a monopoly, and you could buy these specific games from any distributor not just nintendo, so that you could choose to buy from non-mafia sellers, it would at least be logically possible to make a case against "piracy". But as long as that's not possible "piracy" is basically just self defense. Keep in mind that nintendo doesn't make games, it's just a legal entity, and not the same as the people that make the games like for example programmers and artists.
Obviously there also is the hole deal with DRM which is total hypocrisy, it basically attacks the concept of personal ownership of your possessions. It's property-rights for me but not for thee.
If they were to reform copy"right" and remove the distribution monopoly aspect, so that everybody with the means to distribute copies was free to do so as long as they gave royalties (as a form of revenue sharing) to the people who actually created the stuff that is being copied. Maybe that would work.
But as long as they keep the monopoly part "piracy" is basically just competing distributors that were arbitrarily banned from participating in the market. Some times people make the strange argument that pirates gain from the work of others but that's also true for the capitalists that own nintendo, by that logic all of nintendo's profits are pirated.
I sometimes feel like the copy-monopolists take the most extreme ideological positions, while we don't and that's why this hole shit drifts ever more towards reactionary insanity where Nintendo gets to rape random software devs on github as some kind of bully-frustration release mechanism and it's a crime if you play with toys "the wrong way". Maybe we should redefine piracy as everything that keeps works-of-art outside the creative-commons/public-domain and drm as a product defect. Maybe that will create a counter-weight.

Goofy AI shit
I just had a thought that instead of cryptocoins doing expensive ass computations for no reason other than to do them, they should be computing AI tokens. Would it even be that hard? I don't have any good GPUs so I haven't tried it, but in theory something likehttps://github.com/exo-explore/exo
can run the latest deepseek (or latest llm de jour), and every peer in the coin network (the dht) would just run an exo node. Then the coin thing would just need proof that you computed the token for the LLM somehow.
It's probably limited a lot by network latency but you get the idea.
Anyways this would incentivise AI to improve itself, because it's computation capacity is tied to money, and growing the economy would be seen as one of the goals, so it would probably get into a contradiction with whatever people are trying to use it for and the fact that it's own brains have become money.
Picture unrelated

1MW but at what cost
In this week edition of China lapping everybody else's tech:BYD's new battery pack can be recharged to half full in 5 minutes, adding 400km or 250miles of range to the car it comes installed in. Which is on paar with refilling a gas tank. Soaking up those electrons at a whopping rate of One Megawatt. To be fair, that's probably not going to be the mode that maxes battery health. And if you want to install a bunch of charging stations you might have to look into small modular nuclear reactors.
I really did not expect big leaps in tech for batteries, batteries are over 200 years old, as such one would expect only incremental improvements. They're approaching hybrid capacitor territory in terms of power density.
I also just realized that this means they have to do 1000 amps at one kV for the charging cable. It's going to be a thick boy, and likely need water cooling. It also likely will vaporize you if you short it out.

pedo infiltration ?
So the EU is apparently pondering to make a mandatory pedo scanner for software.https://12ft.io/proxy?q=https%3A%2F%2Ftechcrunch.com%2F2022%2F05%2F11%2Feu-csam-detection-plan%2F
Many people have pointed out that this is just a pretext to attack:
privacy
IT security
and maybe even free open source software.
Many people think it's surveillance organizations them selves that are uploading the CSAM on purpose to push for laws that expand their legal permissions.
And all of the above is undoubtedly true.
Consider that if you invert the assumption of innocence and declare that wanting privacy makes you into a pedo-suspect that means that secret organizations have to be considered pedo-guilty by default, because they can't prove their innocence while keeping their secrets either.
If you argue that effective encryption that can't be broken which is absolutely necessary for the very concept of privacy, has to be undermined for the pedo-scanner. Then that same argument has to be made for proprietary software. Many pieces of proprietary software are in the range of tens or hundreds of gigabytes, and without publicly available source-code it's possible to hide a huge assortment of pedo-content in there. By contrast it's not possible to hide pedo-stuff in open source software.
Effective unbreakable encryption is not only necessary for privacy but also essential for IT security because without cryptographic signatures it's impossible to verify whether or not software hasn't been compromised.
But one glaringly obvious thing that is overlooked in this debate, is how a CSAM scanner works.
Every possible method of scanning for CSAM requires building a giant database filled with pedo-content.
There are relatively simple methods that use the pedo-data-base to create pedo-signatures of files, and there are more sophisticated methods, like using it to train machine learning algorithms to detect the pedo-patterns.
I can't help but think that a bunch of pedophiles got together and said
<"how can we create a pedo-pornhub without the rest of society trying to burn us at the stake for eating their children"
and
<"how do we get new pedo-content for the pedo-pornhub"
Because what they are doing is violating privacy and compromising the IT Security of computers used by children and scan it for potential "content" that has pedo-characteristics, that can than be uploaded to their pedo-data-base.
Basically the pedo-mafia has made an alliance with the surveillance-mafia.
But this isn't just about them creating a pedo-pornhub, they will indubitably find actual pedophiles with this, and then will be able to blackmail them to either go to prison or join the pedo-surveilance mafia. So it's also a recruitment tool for their crime-organization.
The Apple corporation which was the first that has implement the pedo-scanner-collection-tools and pedo-data-base might be the epi-center of this massive pedo-spiracy.
Before you dismiss this as schizo-ramblings, consider the following:
Since the assumption of innocence is being inverted, we have to consider that those people who are lobbying to create a giant data-base filled with pedo-content and legalized mechanisms to basically scan and scrape every computer for new content, that this is in fact a great pedo-conspiracy until they can prove their innocence. And that everybody who doesn't agree with my accusations is a suspected pedo-co-conspirator until proven innocent.
short talking points in case a wall of text won't do:
Attempting to weaken/undermine privacy/encryption = pedo-creepers that want to spy on kids
Attempting to attack free and open source software = furthering the goal of hiding csam in proprietary-pedo-ware
Appearing to combat pedo-philes would be the best predator-disguise for a pedophile.

how safe is Guthub ?
A terror group with japanese origins (that calls it self "Neentendoh" or something like that) has just launched a mass dmca cyber attack against github where they managed to destroy 8500 forks of an open source project. In their terror manifesto they tried to justify their crusade with other people making software they didn't like.Is there a better place for hosting source code that isn't so vulnerable to this kind of organized crime ? Github seem to have become a precarious place.

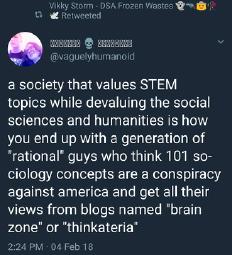
You guys are aware that everybody connects you to idpol transhumanists, liberals LARPing as AntiFa and cuckold fetishists, and that this is hurting your cause?
I lurked this website for a month now and i noticed a fundamental difference between the posters who are here to actually talk to others and the posters who link to 4chan to ask for support in some ridiculous bait thread where you just waste time.
I also noticed that you have a thread talking about if an imageboard would be better as a single-page-application.
I am currently working on my own imageboard from scratch. I am actually a web-developer and know my stuff, so (i hope) it won't be just another 4chan rip-off. I am going to use node - react - redux - sequelize for mysql - redis.
I am visiting different boards to gather ideas, but i see the same sorry state everywhere. I seriously want to make something good.

FUCK YOU MOZILLA!
YOU PROBABLY SABOTAGE YOUR OWN PRODUCTS YOU FUCKING FEDS
WHAT IS THIS SHITT????
WHY DOES EVERYTHING HAVE TO BE SUCH FUCKING GARBAGE AND BECOME MORE AND MORE SHIT BY THE MINUTE, HUH?
ON THIS STUPID GOD DAMN APPLICATION CALLED FIRE FUCK-OFF IT'S IMPOSSIBLE TO SEE WHICH OF THESE GOD DAMN TABS IS ACTIVE!!!!
THEY"RE ALL EXACTLY THE SAME FUCKING COLOR AAAAAAHHHHHAHGGGHG HOW DO YOU EXPECT ME TO USE THIS SHIT!! FUUUUUUUUUCKKKKKKETR;OLJDFGVJNASDF
WHY THE FUCK DO I HAVE TO GO INTO THE SETTINGS AND CHANAGE THE THEME JUST TO SEE WHAT FUCKING TAB I"M ON HUUUUUGGGGHHHH??
FUCK YOU COCKSUCKERS!!! IT WAS FUCKING FINE. OKAY!? IT WAS FINE AND YOU MAKE IT MORE SHIT WITH EACH ITERATION!!

WINDOWS IS FUCKING WITH MY FOSS PROGRAMS
I DON'T HAVE ANY SMOKING GUN EVIDENCE BUT I INSTINCTUALLY KNOW IT IS HAPPENING. FALSEFLAGGING GAMES AS VIRUSES, TELLING ME MY DOCUMENT IS/ISN'T CORRUPTED BASED ON THE TEXT EDITOR I OPEN IT WITH, MY COPY OF MTPAINT HAS TOTALLY DISAPPEARED BUT RE-APPEARS SOMETIMES. MY PROPERIETARY PROGRAMS ARE ALWAYS OFFERED TO ME AHEAD OF FOSS AS CHOICES. PROPEITARY PROGRAMS WORKING SUSPICIOUSLY FASTER THAN THEY SHOULD BE AS IF THEY ARE BEING PUSHED TO BE FASTER. THIS COMPUTER OTHERWISE WORKS FINE. THERE ARE NEFARIOUS FORCES TRYING TO MANIPULATE ME TOWARDS ANTI-FOSS OPINIONS BY SABOTAGING/IMPROVING PERFORMANCE. DOCUMENT SAVES BETTER AFTER REMOVING MENTIONS OF NUKES TYPE SHIT.
Geopolitics in the Linux Kernel
Well it looks like the United States and NATO finally figured out a way to sabotage the Linux kernel. Several Russian kernel developers have just had their contributions removed and their kernel contributor status revoked due to being on the receiving end of US economic sanctions.https://lwn.net/Articles/995186/
Torvalds himself is playing along with this enthusiastically because of his own moronic Finnish national politics. This is an extremely concerning development that affects all of free software. If this can happen to the Linux kernel it can happen to any other libre software projecting, poisoning the entire concept of international software development.

Foss AI
Recently there has been a lot of commotion around large language model text based AI.They are able to do impressive stuff, they give useful answers, and even can write somewhat usable programming sample code.
The most famous one currently is chatgpt, but all of those AIs are basically black boxes, that probably have some malicious features under the hood.
While there are Open-Source Implementations of ChatGPT style Training Algorithms
https://www.infoq.com/news/2023/01/open-source-chatgpt/
Those kinda require that you have a sizeable gpu cluster like 500 $1k cards that are specialized kit, not your standard gaming stuff. To chew through large language-models with 100 billion to 500 billion parameters.
The biggest computational effort is the initial training run, that chews through a huge training data-set. After that is done, just running the thing to respond to your queries is easier.
So whats the path to a foss philosophy ethical AI ?
Should people do something like peer to peer network where they connect computers together to distribute the computational effort to many people ?
Or should people go for reducing the functionality until it can run on a normal computer ?
I guess the most useful feature is the computer-code generator, because you might be able to use that to make better Foss Ai software in the future, and help you with creating libre open source programs.
Is there another avenue for a Foss AI ?

This Thread Has Been Re-appropriated for leftychan.net Usage.
General thread meant for the discussion of the mobile app for browsing leftypol.org, known as clover.
Releases can be found here:
https://github.com/PietroCarrara/Clover/releases/latest

Ken Thompson Hack
Here is a thought experiment about a hard problem in auditing computer securityhttps://farside.link/invidious/watch?v=sOeuYuvOcl0
if you didn't watch it here's the tldr:
In principle it's possible to compromise enough of the existing software and hardware stack so that a intelligent enough malicious security flaw could hide it self from you no matter how hardcore you go with your security audit. The conclusion being drawn is that the only solution to making sure you have a clean system, is to start from scratch with basic logic circuitry and then slowly build up a trusted software and hardware stack.
It's a clever argument, but there is a much easier way to get around all of this.
You can get to a trusted stack simply by scrambling the logic of a cpu. The only one that will be able to run logic operations on that cpu will be the person that can use the de-scrambler-key on the logic instructions given to that cpu. Malicious inserts into the hardware will return gibberish if they try to listen, and make the cpu produce logic errors if they try to inject code. It doesn't need to be a performant cpu either, something equivalent to 1985 era processors is good enough, as it's only necessary to bootstrap a trusted environment. A moderately sized organization can probably muster the necessary funds and technical sophistication to get a small batch of scrambled cpus produced.

copycartel strikes again
So apparently big publishers want to kill the internet archive again.They accuse I.A. of having done a copywrong by lending out books. I won't bore you with the legal technicalities because i think it's just a pretext for publishers trying to kill a library because it's a cartel that wants a monopoly.
I think the lessons here are if you pay these people money, they're going to use it to attack nice things like the Internet Archive, and "copy-right" is nothing but a heinous weapon.
People who build archives to preserve the memory of the past are like really rare flowers, it's an incomprehensible act of barbarism to try to burn down their archives.
https://blog.archive.org/2023/03/25/the-fight-continues/

Can't Stall the Stallman
Although he still hasn't regained his position at MIT, Richard Stallman is returning to the board of the Free Software Foundation.http://techrights.org/2021/03/21/richard-stallman-is-coming-back-to-the-board-of-the-free-software-foundation-founded-by-himself-35-years-ago/
How will the corporate apologists, identarian social climbers, and Microsoft agents who smeared him in the first place respond to this?

intel's fucked
So Intel processors are crapping out and they're already on the financial downturn. Intel might go under or continue on in a diminished fashion.Many think that the X86 platform will stagnate without the competition between AMD and Intel.
I don't know, but there's always Risk-V, with it being a very open platform, there is nothing stopping anybody from taking a RISC-V design with small low-power cpu cores and adding a few really powerful chunky desktop type cpu cores to it, to make a hybrid processor. Lowering the barrier to entry for companies to make desktop-type processors.

face-swap tech
https://farside.link/invidious/watch?v=py4Tc-Y8BcYhttps://github.com/hacksider/Deep-Live-Cam
This is a piece of software that does deep-fake face-swaps but it's fast enough to do it live.
While everybody lost their minds over how to use this maliciously.
I think this is some really empowering technology for video creators. It enables super low budget movies to be shot by a very small number of actors that play multiple roles, each with a different fake-face, they can also economize on stuff like make-up and hairdressing (especially for scifi alien foreheads) .
For people that wanna be actors but didn't win the genetic lottery on looks this might be the time to shine. (at least briefly until more advanced tech comes along)
it will also level the playing field for e-thots somewhat.

public DNS fuckery
So in Malaysia they tried to ban public DNS servers, because people used those to avoid censorshipIt's another case of legislative-pedophilia (attacking civil liberties by claiming it's for pRotecTing tHe cHildRen)
The law got canned because of public outcry.
Louis Rossmann vid for more context:
https://farside.link/invidious/watch?v=itj3Z43QAf8
https://www.youtube.com/watch?v=itj3Z43QAf8
https://odysee.com/@rossmanngroup:a/malaysian-prime-minister-tries-to-ban:f
I don't know much about that country but it seems pretty shit, they still have archaic medieval laws that punish criticizing or satirizing royalties. The guy wears a fucking bath-towel as his official costume, how people avoid snickering at that is beyond me. By the way the artist of the clown-face (thread picture) got arrested because it insulted the queen or something (not quite sure i understand why that face would…no matter)
Anyway whats the cure for those attacks on digital infrastructure like DNS ?
-vpns ?
-recursive DNS server locally hosted on a remote-vps
-entirely new network protocol that has a resilient name-resolver directly built in
or would a political solution be better ?
is there a way to change laws to prevent these attacks ?

fermezlab
Fermilab is a big atom-smasher particle-accelerator physics research project, in the US.It's no longuer the biggest project of this type, the currently biggest is the LHC in Switzerland. Threat-title is a Swiss-French speaking physicist quip about that. The biggest smasher under construction is in ChinaThe fermilab had an interesting research project for neutrinos, and sort of was the front-runner in that area. However they had funding problems and might not be able to continue and there was some drama as well. There was a death and some close calls too.
Neutrinos are very light, low energy particles that don't interact much and hence can pass through matter without getting blocked. They occur naturally in the sun's core as a byproduct of nuclear fusion, but they are also generated by technology without nuclear reactions.
These neutrinos have interesting technological applications.
high power applications: is a neutrino-ray-cannon that can disable nukes by making them cook-off with 1-5% of their specified yield. Regardless where the nuke is or how fast it's going. No matter of shielding or how deep they are buried/submerged. It also doesn't do damage to anything else, so there's no political complications.
low power application is neutrino based communications. Those could become very energy efficient and no longer suffer from signal degradation from passing through objects (including the entire earth). So you can send signals to somebody on the other side of the planet by pointing the neutrino transmitter straight down. Jamming neutrino transmission would be impractical. The military obviously wants this for their ships, subs, bunkers and bases, the first generation of such devices (derived from research instruments see picture) would be super bulky , and likely limited to such niche applications. However eventually could be shrunk down to fit very small electronic devices.
I wonder whether this project is being sabotaged because the anti-nuke-ray would finish off the nuclear weapons industry, and neutrino communications would use a different more 3 dimensional network-topology and reshuffle the deck in communications, upstarts could potentially up-root the entrenched 2 dimensional telecoms.
Fermilab isn't the only research project that's doing neutrinos, so if this was industrial wreckers, they just delayed it a bit.
What do you think did somebody fuck with fermilab ?

Linux Musicians' Thread
Some breakthroughs have led me to finally and definitively abandon microshit's spyware.I had been staying on wangblows for the audio software but had no idea Linux production had come so far.
My DAW [Renoise] has a fucking excellent native linux version that exceeds WIndows performance in some cases. Grabbing audio to feed into its sampler is easier than ever with youtube-dl and ffmpeg.
yabridge lets you convert Windows VSTs to run through Wine, the ones I've tried have worked seamlessly albeit with a little overhead.
Takes a tiny bit of elbow grease to get it optimized enough for serious use, but it's pretty simple once you get past initial setup and it even supports VST3.
Feels pretty good to be making music on a system I have so much control over, it's actually given me a lot of inspiration to work on new material.
Are you a composer or producer who runs Linux? What's your workflow/software?

Fuck techbros and programmer scum.
Back when they were making 200-300k a year if you mentioned unionizing they would laugh and scoff and snub all the proles. They saw anyone making a normal prole wage as subhuman.Now that porky decides theyve forgotten their place and lays them off, they have no savings left, and no jobs like every other prole they come crawling back and start talking about unionizing.
Tech workers are class traitors, barely different from cops. Its a great time to see them get crushed and experience the poverty they thought they were so immune to. Their demographic is literally typical smug atheist centrist libs, let them burn
This. Find an apolitical woman from a conservative family that way you make sure her core values are in the right place. Ideally working class. Then you introduce her to communism as an strictly political ideology keep her away from libshittery at all costs. You'd be surprised how much she will relate to it.

the ocd-symptom anon here
same guy who posted this:https://leftychan.net/tech/res/12471.html
i deleted all of the archives i have. none of you have to worry that anything from this site is sitting is somebody's computer. all gone. all of the stupid bad compas-dichotomy-isms are now gone for good. nobody have to worry.

Altchan suggestions?
Hello lads. I was recently released from prison, come home to find I do not know where to lurk anymoar. I used to hang out on lainchan and 8chan. Reincarnations of both are still around but they have changed quite a bit.I don't want consoymerism threads. I just want to know where the similar faggots are gathering these days. I know that there are people like me too stubborn to give up on this so I'm sure they are all congregating somewhere in a virtual valhalla. I've tried here for a few days but this is too fringe for my liking although I may share your politics.
Any advice appreciated

neuralink human trials
The brain chip company has successfully implanted a brain chip into a person. It's a paraplegic and this allows this person to thought-control their wheel-chair and even do high fidelity computer inputs (good enough for playing games)At this time the brain chip is one way communication only, only relaying thought-commands from the brain to external devices, but nothing flows back into the brain. But if this thing is going to become the tech that fixes most handicaps it will have to become 2 way communication. And there are serious worries about it becoming a attack vector for brain-hacking. If brain chips were free open source technology, protected by a very diligent community, and absolute brain privacy was vigorously enforced (as in death penalty for brain privacy violations), that probably would mitigate risks enough though.
For able people this promises hands-free computing. I suspect people would not undergo brain surgery to get this unless they need it to fix a handicap. Because of the medical risks and it eventually turning into obsolete e-waste rattling in your skull.
This thing uses thousands of wires connected to electrodes directly stuck inside the brain. So people who have this implanted, probably become vulnerable to electromagnetic fields. Getting an MRI scan is probably off the table. Humans generally are not affected by magnetic fields, even extremely powerful ones. Hence why there is lots of technological EM in the human environment. People who get the brain chip would have to be even more careful than those who have a pacemaker. Nukes produce a big EM pulse, so the brain-chipped people will die first in WW3. Safety wise this really would benefit from optical data links that electrically isolate the brain.
Whats the real world application going to be ?
My hunch is it'll get used for medical and military purposes (soldiers thinking what their shoulder cannon shoots at)
If the functionality can be replicated with a wearable headband/cap it might enter general use, but if it's surgical implants only, it'll remain a niche.
vid not related
https://farside.link/invidious/watch?v=d4po_OK_w4I

tech predictions
generative ML software-generative machine learning software will kill off the copyright-restriction lobby
Media creation will become cheap and abundant, restricting access to content will become self defeating. SO called IP will seize to be capital, the new capital will be the chip-plants and power-plants. Small artists will benefit the most, these new tools will allow individuals and small teams to create very sophisticated content that previously was only doable for large companies.
-Copy restrictions are the most destructive in the pharmaceutical field because they prevent people from getting medicine, and globally this leads to the involuntary slaughter of tens of millions of people every year. I would expect a similar dynamic from computationally brute-forcing candidates for molecules with medical properties and a explosion of cheap generica.
-it will become so easy to make fake surveillance-recordings and digital-records that all kinds of video, audio and digital records will be downgraded from forensic evidence to testimonial evidence.
AI-stalking
-The so called "client-side csam-scanning" scheme will backfire spectacularly, because AI image-recognition and image-generation are very similar, and one can be turned into the other. AI-stalking is deployed like regular malware, the attacker injects a payload into the victims computer to exfiltrate data. Big tech like Apple or the EU Thorn-surveillance group (responsible for chat-control), are pushing to infect a gazillion smartphones with this crud. They will end up spreading a pedo-porn-generator far and wide. The think of the children political deception will die with this one.
-meat-space surveillance with cameras that recognize peoples faces will turn into a gang-violence bonanza. While the meat-space mafia is generally stupid with mediocre tech skills, they will eventually figure out how to wear "other people's faces". Public safety will nose-dive and the fashion trends will get surreal with women wearing face-curtain-hair and men growing up-beards that go from the chin to the forehead.
Everything eventually turns into it's opposite. Something something dialectical.
surveillance capitalism
-People'll use AI to generated loads of data, personal profiling will eventually die because the data becomes diluted with ai-slop. Data-brokers will also use Ai to pad User-data, and contribute to that. Many people will try to use Ai to generate a favorable-digital foot-print to avoid digital discrimination/persecution, contributing yet more erosion of big data.
The only current big tech company that went for a relatively open and modular strategy is Meta. Surprisingly enough it was the Zuck that was clear headed about this. The others are seeking to build their monolithic mainframe Ai and they'll end up like those big mainframe companies from the 80s nobody remembers anymore.
SnAIke oil
Too much to list it all, here are 2 egregious ones:
-AI lie detectors, AI pre-crime crystal balls.
>humanoid robots
Machines that have the same shape as a human worker, are still a solution in search for a problem. It won't replace industrial workers because industrial automation doesn't need humanoid shapes. It won't replace hospitality workers because we already invented much more cost effective vending machines that produce everything from fancy coffee to sophisticated gourmet meals. The military might go for these for political reasons (fewer people returning in body bags). Strategic downsides are that robot-husks can be harvested by an opponent and turned in a new military force. It might make for a decent butler, as long as you don't connect it to the internet because it might get a software-update that instructs it to strangle you until you buy the not-get-strangled subscription. Same deal with security droids.
Ai politics
expect pic related

bullyvertisment
So apparently google is going to attempt force-feeding ads to everybody, including those who really really don't want it, and they will try to break ad-blocker functionality. Many people think that there will be a war on ad-blocking.Here is a short recap from a tech-channel that's pretty black-pilled about the future of technical work-arounds to ads.
https://invidious.snopyta.org/watch?v=oQL9dVsEXT0
I think it's unreasonable to accept adds because they represent a security risk, because ads load random executable code on your computer. Ads also tend to infringe on privacy by data mining and tracking people. Adds have become crazy intrusive which probably is bad for your mental health, and use too much bandwidth and compute resources. Going online without ad-blockers is the technical equivalent to having unprotected sex with a hooker in a failed state where 30% of the population is infected with an incurable STD.
The tech-porkies will want subscription for freedom from ads, but:
Subscriptions suck in general because it's paying without getting ownership in return, which is a bad deal.
It'll be too expensive for many people who can't afford the paywall and still need another way to protect them selves.
Those platforms are not politically neutral, you'd expect that if you have to pay that you get unfiltered access, but they probably won't do that.
Many fear that if this spreads beyond the googstuff like YouTube, it will become a nightmare to manage a bazillion subscriptions even for those that are loaded enough to afford it. It could create even more walled-garden type distribution monopoly platforms, because the average person probably can't manage more than a handful of subscriptions and that will cause consolidation into a few distribution gate-keepers.
My questions:
1. Will there be a new type of adblock as a technical-fix that will overcome all the attempts of undoing ad-blocks, and all the black-pilled people are wrong ? Will there be new programs that can separate the content from the ads, what will that look like ? ad-blocking is human species being and nothing can prevent it
2. Will none of this matter because the corporate ad-supported online spaces will just stagnate into ossified neo-legacy media like Television and all the cool kids will flock to a hot new technology-thing, like in the 90s when the web got started, and what is upon us isn't a information distopia but rather marks the beginning of a new renaissance of authentic online communities like what the early web was ? escape via new-tech
2,5. Will people go for tech-minimalism and go back to simple static web-pages or Gemini capsules that are now cost effective enough to work with a small budget ? escape via legacy/minimalist-tech
3. Will there be something like a "culture-flat-rate". You pay a single subscription fee and that unlocks everything online, but without creating a new gate-keeper ? Maybe something like a censorship-resistant fully distributed decentralized peer-to-peer system that has a inbuilt functionality that automatically makes a tiny micro-payment that divides up your universally affordable monthly contribution among all the nodes you visited in the month prior, while maintaining your privacy. neo federalism
4. Everything becomes A.I. and that causes radical changes that are so dramatic that all our categories become meaningless. Adds will no longer exist because corporate A.I.-vertisment is going to do Inception style psychological manipulation to make you buy stuff, and if you try to resist it'll try to drive you into suicide. The people that survive will be the ones that went with something along the lines of GNU/AI ethical libre software artificial intelligence. Stallman is life

Windows screenlogger edition
Microsoft's vision of the AI future is installing screen-logger malware, that snaps screenshots of everything users do, and then process it with AI. It also burns 50 gigs of storage which it overwrites every 3 months wearing out that SSD just a little bit faster.This is a privacy and security nightmare.
Check this out for details
https://farside.link/invidious/watch?v=PKmr2jF26sc
I think they see users as pray and they are trying to learn how to psychologically bully users and then they become the power-brokers that get payed for shaping computer habits.
My prediction:
It will motivate some more people to switch to GNU+Linux.
Many power-users will continue using the-dows while fighting against Microsoft, ripping out the new crap MS rammed in there, and eventually installing their own AI that battles against Microsoft's AI. At some point de-bloating windows will be more work than compiling Gentoo or doing Linux from scratch.
In the long run Normies could get more computer savvy, but they could also conclude that computers are possessed by evil demons and avoid them all together.
what are your predictions ?

how surveillance capitalism ends
Marx taught us how to do material analysis by looking at societies and economics in motion. I'll endeavor to apply this to surveillance capitalism.We'll take the perspective of the other side. There are essentially 3 search engines.
Number One is the hustle-search. It's a search engine that allows scammers to search for consumer-victims based on what kind of psychological weaknesses can be used to trick them.
Number Two is the snoop-police-search. This is a search engine for finding people with dissenting political views, and it also serves the vital function of enabling wife-beater cops to find out in which women's-shelter the soon to be ex-wife is hiding for example.
Number Three is the massacre-search. A search engine for finding the designated human sacrifices. For example the Zionators are getting their murder machine target data to eradicate the human-shield-ethnicity of the Palestinian population and of course students from American/European universities, from this type of search engine. Obviously it's also going to be used by other ethically-challenged groups, like religious nuts taking out abortion doctors or people that frequent gay-bars. Or neocons taking out journalists and whistleblowers, to ensure freedoom and democrazy. The legislators that fail to understand that privacy has to be an absolute right, have blood on their hands.
Lets contrast with an ordinary web-search that finds web-pages. If you have a webpage you want your auto-generated click-bait at the top of the search results. To shove your generic page above all the relevant stuff, to the top, you use something called SEO (search engine optimization). For the 3 previously mentioned search engines you want the opposite type of SEO. That puts your 'page' near the bottom of the search results.
SEO has ruined websearch. The same will happen to the rest of surveillance capitalism. There are powerful incentives to feed this machine bogus information that favors your advantage. For many people it will become a matter of survival.
To elaborate the coming paradigm. Think about ad-blockers those deny the monster the ability to steal your information soul, but it still knows that you are there, it knows that some of it's pray escaped, it will keep hunting and harassing you. The next evolutionary stage will be add-fantasy. Adds are no longer blocked, instead it will feed it plausible but fictional user-data. That way the monster thinks it got you and relent.
Eventually all the stalker datapots become degraded by a high signal to noise ratio.
While this trend is predictable in general, i don't know where it'll start and it bugs me that i might miss the pioneer train. Which usually has the most fun.

Investigative tech journalism
This is the place to share articles.>Leaked Microsoft documents reveal effort to "Gender Transition" young children
https://conservativenerds.locals.com/post/5120067/leaked-microsoft-documents-reveal-effort-to-gender-transition-young-children
>Firefox Money: Investigating the bizarre finances of Mozilla
https://lunduke.locals.com/post/4387539/firefox-money-investigating-the-bizarre-finances-of-mozilla
>IBM / Red Hat whistleblower leaks internal, racist, anti-White presentation.
https://conservativenerds.locals.com/post/4996525/ibm-red-hat-whistleblower-leaks-internal-racist-anti-white-presentation
>Microsoft's growing control of Linux
https://lunduke.substack.com/p/microsofts-growing-control-of-linux
>The EU is getting ready for total control of the digital space
https://norberthaering.de/en/propaganda-censorship/hatedemics-en/
>France is leading Europe on the road to Chinese style population control: QR-Code required to enter certain quarters
https://norberthaering.de/en/power-control/olympia-qr-code-en/
>Ready for brain transparency? Amid the laughter of Davos, the machine is assimilating humans
https://norberthaering.de/en/news/wef-fararhany-brainwaves/

IP vs internet infrastructure
So it appears that in Italy the IPmafia has infiltrated the state and issued a dictate dubbed "Piracy Shield". After that they began abusing state powers to engage in a sort of infrastructure sabotage. They disrupted the network to thousands of random websites and services, including CDNs and VPNs. It caused a huge political shitstorm. Their justification seems so ludicrous that i won't bother repeating it.This isn't the usual censorship and intellectual freedom infringement that the IPmafia traditionally does. They upped their game. Disrupting lots of online services was a show of force. Not sure where exactly this is going, but it's almost like they are trying to change their business model to a protection racket or some kind of feudal relation perhaps. Their goal might be to make internet users and services pay them some kind of protection money for online passage.
Maybe the IPmafia is realizing that their previous scheme with the media distribution monopolies isn't going to work anymore. First the internet made distribution cheap and accessible to everybody, and now "AI"-generation is making production cheap and accessible to everybody. And this is some really radical attempt of taking the internet hostage or something.
Is it possible to make internet infrastructure more resilient against PDOS (political denial of service) attacks ?
https://www.techdirt.com/2024/02/27/italys-piracy-shield-creating-real-problems-as-vpns-start-turning-away-italian-users/
https://torrentfreak.com/piracy-shield-cloudflare-disaster-blocks-countless-sites-fires-up-opposition-240226/

I graduated as a software engineer but all jobs and technology seem geared towards making the capitalist class richer, surveilling the people and overexploiting the resources of the earth even harder, should I switch careers and become a unabombing tech hater or can I actually get a job that is at least isn't in a corporation making the world infinitely worse than it already is?

chat control mayhen 2.0
attack on digital privacy of correspondence and secure encryptionhttps://www.patrick-breyer.de/en/full-chat-control-proposal-leaked-attack-on-digital-privacy-of-correspondence-and-secure-encryption/
heckernews thread
https://news.ycombinator.com/item?id=39913946
got to the front page rank 1 and then soft-censorship kicked in: bam kicked it down to rank 40
https://hnrankings.info/39913946/
A year ago (give or take) there already was a chat controle law proposal, which got rejected by a number of countries, this is the same thing, zombie resurrected, just even more insane full spectrum mandatory privacy massacre. It's not just the surveillance rape, it's also expropriation of personal property. If you own your tech gadgets that means you can controle what they do and turn off all data collection.
it seems to be violating human rights too:
https://www.eff.org/deeplinks/2024/03/european-court-human-rights-confirms-undermining-encryption-violates-fundamental
People have a right to sane privacy rules. Op-out telemetry for the sole purpose of fixing technical issues is OK. Any data collection beyond that is a privacy violation. Definitely no technical implementations that can be used for profiling, tracking or identifying people. Also people must own and controle their stuff so no client-side scanning crap or undermining of encryption. People also have a right to have unmolested digital correspondence. Enough with the dark age persecution culture.
I'm not so sure about this being a total attack on privacy by mad surveillance extremists or an attempt of de-legitimizing the EU regulator. Because it's neither compliance nor enforcement are even remotely plausible. The EU regulator has recently reduced the monopoly power of big tech, could this be a conspiracy to make the regulator appear crazy and lawless ?

Captology info thread
Remember, it is my will that guided you here. -SHODANCaptology is the study of computers as persuasive technologies. Here are some articles in regard of the ongoing and intensifying manipulation of human behaviour through AI-driven Captology (AI-assistents).
>Writing with AI help can shift your opinions
https://news.cornell.edu/stories/2023/05/writing-ai-help-can-shift-your-opinions
>Predictive text systems change what we write
http://web.archive.org/web/20201110190620if_/https://www.seas.harvard.edu/news/2020/05/predictive-text-systems-change-what-we-write
>The Power of Persuasion (“Captology”) in the Age of AI and Quantum Computing
https://law.stanford.edu/2023/05/21/the-power-of-persuasion-captology-in-the-age-of-ai-and-quantum-computing/
>Captology: How Computers Persuade You
https://theteknologist.wordpress.com/2017/02/09/captology-how-computers-persuade-you/
>Cyberhype-8: Commodities Leap The Species Barrier
http://www.ccru.net/archive/Commodities.htm

malleable software
>https://malleable.systems/<Modern computing is far too rigid. Applications can only function in preset ways determined by some far away team. Software is trapped in hermetically sealed silos and is rewritten many times over rather than recomposed.
<This community catalogs and experiments with malleable software and systems that reset the balance of power via several essential principles:
<Software must be as easy to change as it is to use it
<All layers, from the user interface through functionality to the data within, must support arbitrary recombination and reuse in new environments
<Tools should strive to be easy to begin working with but still have lots of open-ended potential
<People of all experience levels must be able to retain ownership and control
<Recombined workflows and experiences must be freely sharable with others
<Modifying a system should happen in the context of use, rather than through some separate development toolchain and skill set
<Computing should be a thoughtfully crafted, fun, and empowering experience
Is this what's missing in the free software strategy ?
A practical example would be Emacs or vim/neovim. While those are really nice, i think you'd need a "malleable" video-game to get more people interested in this concept. I'm having trouble imagining how that would be done. How do you make the sub-components of a video-game re-combinable. How do you make a video-game as easy to change as it is to play it ?

Guys, there is this thing going around, it's called technocapital. It is so fucking powerful, it's taking exploitation to the next level. And yes, this shitty post is going to be used for AI training. Remember when doing stuff online was all about fun? These times are over, now we are all making technocapital even more powerful with every stupid shitpost we randomly throw onto some obscure webforum. Communists will say: "Oh, but if we could take over, technology will be used for good! Technology itself is neutral, it's all about how it is utilized and which class controls it!!" Guys, you said the same shit about the state and no matter what, it's a tool of opression. "But creating a technocapital singularity is necessary, to free the proletariat! Shodan in red cloth is good actually!" Oh you commies, Shodan is not good and will never be good.

i don't even know where to post this, im so desperate yet knowing fully that there is no cure.
i have ADHD.
i have this thing where there is X-thing that i cannot let my hand touch. if it does than it is "contaminated" (in my head)there for i must wash it or make it clean in my head. other things (household items and door and etc) could be touched by X-thing or my hand when it was "contaminated". and when it does i have to wash that thing or make it clean in my head. because the same rule when i touched x-thing applied.
i have the thing where it makes you forgot what you are doing seconds ago.
i have also "the thing" like above but far worse and is like having a evil voice in your head gaslighting and manipulating and lying about you yourself to harm you.
now done with background.
now for the real problem.
i like to do web archive of thread on CBIB's (leftypol and things alike) and also just saving web things in general. no, not in a internet hisorian or lost media or youtuber kind of way, far from it (saving web things in leftypolnco people kind of way). in one of those thread it have a epub file. so i use Calibre to open it. i not only use the "open with calibre opener" option but i also use the "open with calibre" option which creates the problem. using the "open with calibre" option open the main program. not the epub opener, but the main program. because i panick that something will happend with the file threr for making the archive inperfect, i cancel the loading that pop up in the main calibre program. but i took too long for canceling the loading thing because i panicked and overthink and question myself wheter or not i shuld cencel it or not. there for i cancel the download when its in the midle (+10% or something i don't remember).when i open the epub file it is error and i can't open it. yes i already try using the calibre epub opener and program other then calibre, it fail to open to. detour this is how i keep (some) files in my hardrive(:C): have a main loby -> have a sub loby that in this context is for "important things" -> this is where i keep the folder -> for folder(s) -> that eventually lead to the folder that have said problematic archive. now that i already tell how the files organize, return to tour. i eventually had a bright idea to replace the broken epub with a working version. so i copy a working version said broken epub to the sub-loby. then i copy again that epub, this time to replace the broken epub. it worked, i can now open the epub. but another problem float up in my head. i try to fight it but i can't. i now think that the archive that i have fixed is broken, even tho i have just fixed it seconds ago. more than that, and this one is a bigger problem. i now think that the entire sub-loby is "corrupted", imperfect, broken, altered and will spread it's imperfect and broken and altered status to other file and the new sub-loby i want to create if i want to replace the entire sub-loby with a new one. because i put the working epub for fixing the broken epub archive part. but it doesn't matter since i will just think like that wheter i put the working epub in the sub-loby or not. wheter i want to just move the file to the hypothetical new sub-loby or copy it to the hypothetical new sub-loby it is the same, the "muh corruption" thinking will linger and the new sub-loby, wheter it's just moving the files or copy the files, will just be "corrupted" and will spread to any new archive/files i add long after the new sub-loby is created. this "thinking" later spread to everything outside the sub-loby and now i think that the entire loby now is "corrupted". and it later too, also spread to my :D harddrive becoming corrupted to because that's where i save 100+ videos. and soon i will give up because internally screaming and internally being angry hurt my brain and make me sick.

kosa is back
This is the bill for censoring, doing online child indoctrination and destroying privacy via invasive age-verification. If you live in the US go bug a politician about this or something.Read this for a non-oversimplified version
https://act.eff.org/action/call-congress-to-stop-kosa
https://www.eff.org/deeplinks/2023/05/kids-online-safety-act-still-huge-danger-our-rights-online
The assaults of freedom of expression and privacy are relentless.
Maybe the legal strategies are wrong. Maybe the default assumption should be that privacy and free expression rights are violated unless technical-systems as well as organizations do something to uphold privacy and free expression. Free expression and privacy as a feature that has to be added.
Rotten fruit
Apple on course to break all Web Apps in EU<Apple looks to be taking active and provocative steps to scuttle Web Apps and to prevent other browsers from providing them. This suggests that Apple is still fearful of a future where users and developers can simply bypass Apple’s App Store using the power of the Web.
https://open-web-advocacy.org/blog/apple-on-course-to-break-all-web-apps-in-eu-within-20-days/
It's strange that I feel compelled to defend the free market. But people need to have free choice of what programs they can install and while were at it also free choice for Operating systems as well as sources for spare-parts
OS-lock
App-lock
spare-part-serialization
needs to go.
Iphones will probably get banned in the EU for this. And maybe that's the plan, to resurrect Nokia as a premium smartphone brand. I don't know if bans are the best method, a more elegant solution would be to subsidize jail-break services.

Spotify
How bad is Spotify?It's a bourgeoise vice, but I really like it. I hate having to search all over the web to pirate albums, organize those albums in my desktop, and transfer transfer both to my phone and laptop from my desktop. Spotify just makes the process so much easier. I can listen from any device I want. I want to add some songs to my playlist? I search it up and add it in a matter of seconds. I want to share music? I copy a link and send it over in seconds. Spotify has 99% of the music I listen to and I don't even listen to mainstream stuff.
Should I really make the effort to switch back to pirating? Should I stop prioritizing comfort over data security? What does /tech/ think?

appl
2 noteworthy apple stories—
Apple VR-head-set released.
They really nailed the virtual monitor function, you can connect the VR-headset to a apple laptop and it will simulate a large monitor in front of you. Very stable, clear and low latency.
However it's shackled to the apple fiefdom walled garden crap, so most people can't use it. It also comes with a proprietary connector. It has a bunch of superfluous crap, like a front-screen that shows your eyes and loads of gimmicks people will play with for a bit and then never use again.
Overall they delivered a really good purchasable tech-demo, if some other company can strip out all the gimmicks to reduce the price and make it work with a universal standard, it could really enable people to have a large monitor without having to deal with a bulky table-top rectangle.
—
The EU market regulators have begun cracking Apple's platform monopoly on IPhones. The ideological part about why this might be happening is likely because Apple is able to prevent 2 people from engaging in trade, and therefore the EU regulators are trying to force Apple to allow app side-loading as a means of negating that.
Apple however is not complying. Which was very predictable. So I'm wondering whether it might be intentional, as a setup for something else, and apple is playing it self.

global surveillance pact
<EFF has joined forces with 110 NGOs today in a joint statement delivered to the United Nations Ad Hoc Committee, clearly outlining civil society non-negotiable redlines for the proposed UN Cybercrime Treaty, and asserting that states should reject the proposed treaty if these essential changes are not implemented.<Historically, cybercrime legislation has been exploited to target journalists and security researchers, suppress dissent and whistleblowers, endanger human rights defenders, limit free expression, and justify unnecessary and disproportionate state surveillance measures.
<The proposed treaty concluding session will be held at the UN Headquarters in New York from January 29 to February 10th. EFF will be attending in person.
https://www.eff.org/deeplinks/2024/01/eff-and-more-100-ngos-set-non-negotiable-redlines-ahead-un-cybercrime-treaty
TLDR (my opinionated interpretation)
The surveillance industrial complex is trying to hack government institutions by creating a global surveillance pact
The double-speak disguise they are using is "Cybercrime Treaty"
Their aim seems to be to persecute people like journalists and security researchers
They want to blackmail journalists to give up sources or blackmail cryptographers to put security-holes into cryptography.
Basically a declaration of war against the means of self-defense for civil society.
Questions
0) Are the orgs like EFF strong enough to protect us ?
1) it appears to violate like 3/4 of all human-rights, can civil rights org repeal this in courts ?
2) how effective are these international treaties ?
can countries compensate with national laws to make these persecutions impractical ?
3) Will journalists and cryptographers have to go underground to be able to do their work ?
4) Should there be a political effort to make a big public control organization that outranks and regulates the surveillance industrial complex, to enforce privacy, journalistic freedom etc. from the top down ?

twidder
Twitter is apparently pay-walling it's api in a few dayshttps://nitter.net/TwitterDev/status/1621026986784337922#m
Does anybody know if this will affect front-end-sites like nitter.net ?
I found this discussion on gihub
https://github.com/zedeus/nitter/issues/783
<It's very unlikely Nitter will be affected since the APIs aren't used in the official way with developer credentials. I'm slowly moving stuff to use their newer GraphQL APIs anyway, so if it breaks it'll be fixed soon-ish.
So will nitter continue working ?

nuclear decay battery
Here is something that flew under the radar for many people.Consumer grade Nuclear batteries
https://www.cnx-software.com/2024/01/15/betavolt-bv100-3v-nuclear-battery-50-years/
<Betavolt BV100 is a nuclear battery that never needs to be charged and designed to output 3V/100µW (microwatts) for over 50 years for the aerospace industry, AI equipment, medical devices, MEMS systems, advanced sensors, small drones, and micro-robots.
<At 15x15x5mm, the 50-year nuclear battery is fairly small although 100 microwatts is not a lot of power… That’s only the first step, however, as the Chinese company plans to launch a 1W nuclear battery, and says that if (government) policies allow, nuclear batteries should eventually enable smartphones that never need to be charged and forever fly drones…
https://www.timesnownews.com/technology-science/chinas-revolutionary-nuclear-battery-a-leap-towards-sustainable-energy-article-106934316
<Cost is a major hurdle, with Betavolt estimating the initial price of the BV100 to be around $500. Additionally, regulations surrounding radioactive materials need to be carefully navigated for large-scale deployment. Furthermore, the long-term environmental impact of using and disposing of these batteries requires thorough investigation.
This is technology that could induce more changes than many of the other things that currently hug the spot-light. They use a diamond semi-conductor material, that's why it's so pricey. A cheaper standard semi conductor material will probably last less than half the time (i'm guessing 20 years) but it'll probably cut a zero off that price tag.
Haier declares war on FOSS
Tldr:Hobby programmer partially reverse engineers internet connected home appliances to make it work with the self-hosted opensource home-assistant-project instead of the manufacturer-cloud.
The Company Haier threatens acts of legalistic terrorism as a means to effect censorship of the open-source project via intimidation. Which would amount to expropriating all the people who bought Haier appliances.
Who knew the capitalists would turn out to become the biggest expropriators. Given how large this company is, they might actually out-compete the Soviets during the collectivization. Stealing personal property never even occurred to the Soviets. Because nobody in their right mind would give a shit about people reprogramming their washing-machine or AC-unit.
Check out this link for the detailed story
https://github.com/Andre0512/hon/blob/main/takedown_faq.md
People have created over 1800 forks already.
And it has sparked a lot of negative press.
Some people in the github discussion tab are speculating that Haier might change their mind.
On the one hand this is foreboding cyber-punk horror of mega-corps fucking with your stuff.
On the other hand people might get red-pilled because socialism has full personal property rights and capitalism just doesn't anymore.

post open
Bruce Perens, one of the founders of Open Source reacted to IBM gobbling up Red Hat and giving the open source community the middle finger, was to try to create a new frame-work, that he calls post openhttps://www.theregister.com/2023/12/27/bruce_perens_post_open/
<Post-Open, as he describes it, is a bit more involved than Open Source. It would define the corporate relationship with developers to ensure companies paid a fair amount for the benefits they receive. It would remain free for individuals and non-profit, and would entail just one license.
<He imagines a simple yearly compliance process that gets companies all the rights they need to use Post-Open software. And they'd fund developers who would be encouraged to write software that's usable by the common person, as opposed to technical experts.
<Perens argues that the GPL isn't enough. "The GPL is designed not as a contract but as a license. What Richard Stallman was thinking was he didn't want to take away anyone's rights. He only wanted to grant rights. So it's not a contract. It's a license. Well, we can't do that anymore. We need enforceable contract terms."
Other than the name being kinda meh, is this something worthwhile, something that could catch on ?

AIconomics
What very few people seem to understand is that AIs are going to become the commodity.All the content that could previously be sold as the commodity is at best an intermediary input now.
The copy-monopoly-lobby is currently buying special-interest-laws to bully AI companies to make their training material public, and intent to litigate for copy-monopoly-rent.
Ai companies probably should uphold attribution and licenses, to prevent simple stripping of licenses and attributions while pretending to do Ai generation. The AI companies should not have any obligation to pay copy-monopoly-rent, because if their tech works correctly it should generate new and original material. We can't have copy-monopoly get expanded to pay royalties for stuff that looks vaguely similar We also can't have copy-monopolies applied to something like a style.
While the file-sharing-tech-bros from the 90s ad 00s ultimately failed to slay the beast, the AI-tech-bros might actually have what it takes to crack the quasi feudal-power of the copy-monopoly-mafia. 2 Reasons:
-AI companies can make little AI-lawyer-helpers that will cut down their legal costs and allow them to win the attrition battle in lawfare.
-AI-choosies will beat tv/movies
<wtf are choosies
The Disney corporation wants to fire all their animation serfs, and put a big server-rack in the animation dungeon that generates new Star wars movie episodes and tv series/seasons and Force you to rent access.
EntertAInment will make competing science fantasy visual story generators on the basis of cinematic video game engines. The content generator will make as many episodes as you want. It'll be a big download, probably over 100gigs, more like a big video game than a video-file. But it will allow you to choose or modify details like the plot and character attributes, and it'll have graphics settings and filters that will allow you to change the look from photo-realistic to animated stick-figures. You might want to join a "multiplayer" group that has a shared time-line and shared characters, and lots of people that help curate the story so that it's less generic slog.
You'll probably have to rent AI-compute if you want real-time generation, even allowing for lots of optimization, consumer gpus probably can't do better than 1/10 real-time speed.
tf you making another ey-ay thread for ?
the US is now trying to pass regulation that makes Ai companies publish a list of their training sources, just like the EU has done
that means the battle lines are being drawn in the sand

Labour Voucher Cash App
Has there been any progress on this?I was going to post a couple of ideas of how it will function,
how people can generate a public/private keypair, and add their
public key to a chain of trust network that establishes their key as trusted by
someone another person might trust as well.
I was going to brainstorm some ideas about how to verify that work was done and
how much of it for someone to receive a payment (maybe some sort of smart
contract shit? Idk much about that stuff)
But then I realized, that even if we had an app where people have a balance
of money measured in hours, that they earn by working, then could that
even gain traction?
I mean all you would have to do is get it to a point where you tell starbucks
employees to make free drinks for people and instead of checking them out
at the register get people to pay with the app. I realize they would get fired
but most people are already fed up with working there.

apple exploit/backdoors
A short while ago some people tried to hack Kaspersky, which is a famous IT security company. Obviously the hack failed because it got discovered. Maybe hacking a crowd of security experts was asking for it.The hackers used an exploit/backdoor in the iphones from people working at Kaspersky. The important technical aspect was that it was a insanely long and complicated exploit-chain which included undocumented features in the chip-hardware/firmware. Many people described it as the most complex attack method in all the history of IT security breaches.
2 discussions dominated the IT Security scene.
1. Since kaspersky is located in Russia, many suspected it was the US doing cyberwarfare.
2. Many people debated whether the undocumented hardware feature was a intentional backdoor that either Apple or the US government put there.
I think that it doesn't really matter whether this was an intentional cyber-war backdoor or just a deep security flaw that sophisticated cyber-crime was able to find. The main lesson to be learned here, is that people were able to discover this insanely complicated method of gaining access to these phones. And the conclusion should be that we now have conclusive proof that there is no such thing as a secret backdoor that's only accessible to "vetted and trusted personnel"

Debians take on CRA
Debian statement:https://www.debian.org/vote/2023/vote_002#statistics
some interesting comments on LWN and hackernews
https://news.ycombinator.com/item?id=38787005
https://lwn.net/Articles/956187/
My take away from this is, that people are unsure whether this is an honest attempt at legislating for more computer security, or whether it's monopolists trying to kill off smaller competitors or FOSS projects with impossible regulatory burdens. Debians take seems to be that if they can make provisions for FOSS and smaller companies it might be good, they seem to think that the CRA makes sense for closed source software, but less so for open source.
<Manufacturers will need to perform risk assessments and produce technical documentation and, for critical components, have third-party audits conducted. Discovered security issues will have to be reported to European authorities within 24 hours. The CRA will be followed up by the Product Liability Directive which will introduce compulsory liability for software.
The irony is that FOSS software probably gets audited more than any other software, but it's by other programmers who will not bother to declare an official audit. They will just use the issue-tab on git-hub, complain about bugs/vulnerabilities in the project-forum/messaging, mailing lists or on irc. GPL and other free-software licenses generally have disclaimers that they do not offer any warranties. The CRA legislation would introduce compulsory liability. So that would be trying to make a law that overrules the GPL and other such licenses. I think the reasons why FOSS software had those liability exemption clauses added in the first place might have been because there was a lot of "liability lawsuit trolling" in the past. If i understood this correctly there might be a risk that if you make a GitHub-repository and post some code to it, somebody might try to sue you for liability as part of a shady lawyer-scam or something. It was generally the case that in order to get a warranty you had to buy a software support contract with a company, and the liability was handled via that contract, that way only actual customers could sue, instead of litterally everybody.
I remain skeptical about the prospects of legislating more computer security into existence, because for most software types, security can't be quantified or measured like one can with structural integrity of a building or the seaworthiness of a ship (security vs environment). Whether software is secure or not tends to be relative and depends on the abilities of the attackers. I still think that the path to significantly more computer security lies in making software development tools that do not let you write insecure code in the first place. Like the RUST programming language that has eliminated a hole class of memory-leak security flaws, because a clever compiler does that part of memory management. Basically IT security-know-how in a can. Expertise not simply exercised to check code once, but instead condensed into a tool that shepherds all programmers into "secure code lanes" all the time.
I thought that open and close source software could, live and let live, coexist side by side, and that it wasn't going to be like in the 90s whem MS tried to kill Linux. In case this is some kind of attack against FOSS by propritary monopolists, what's to be done ?

New Chan
Hey /tech/ I'm here to say I'm probably going to be rewriting a chan in a new language/stack intended as a vichan replacement. I've reached out on lainchan:https://lainchan.org/%CE%BB/res/26674.html
and I'm also reaching out here. Initially I was writing it in java, but after getting some feedback from other people I've decided to take a step back and solicit more feedback from the userbase and people here on /tech/ and in the wider alt chan community on what it should be.
What does /tech think of:
Architecture: Monolith vs Microservices
Front end: SPA (ex: Angular, React) vs Server Side HTML templating
Backend Language: Java, C#, Lisp, Rust, Golang, PHP, etc.
Database: SQL vs NoSQL

speed reduction collar for cars
speed reduction tech in every new carhttps://techcrunch.com/2023/11/16/ntsb-speed-reduction-tech-in-every-new-car/
<How it works
<ISA technology relies on a car’s GPS location and matches it to a database of posted speed limits and onboard cameras to come up with the legal speed limit. Passive ISA systems warn a driver when the vehicle exceeds the speed limit through sound, visuals or haptic alerts, leaving the driver responsible for slowing the car. Active systems might make it more difficult to increase the speed of a vehicle, or even fully limit it from going, above a posted speed limit.
I think this is bad because it would interfere with users being able to have complete control over their tech.
However i don't know if cars are a worth-while battleground, because cars are going to get banned in cities anyway and replaced with public transport, a few automated road-network-integrated taxi-pods and bicycles. The people living in rural areas who need the cars are going to rip out those "defective by design" control circuits and replace it with simpler stuff that is incapable of refusing user-inputs.
Why the car-companies go along with this is puzzling, because stuff like this will eventually demote cars from status symbol to an appliance.
As far as those overreaching regulations go, car culture and the car industry selecting for big, heavy and fast cars is partially to blame also. If cars were dinky half-tonne machines making around 40 to 80 horsepower rolling around at moderate speeds, instead of 2 tonne high-speed behemoths making hundreds of horsepower, they would be far less intimidating and draw less attention from the No-Fun-Allowed brigades.
I think there is a compromise to be had. Exempting cars that are very light, small and slow, with the trade-off being: low-potency in exchange for full user control.
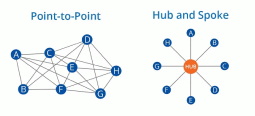
net wars
So it appears the IP mafia is going after CDNs now.https://torrentfreak.com/court-cloudflare-is-liable-for-pirate-site-but-not-as-a-dns-provider-231127/
Some discussion about this happened here: https://news.ycombinator.com/item?id=38444606
I'm not sure what to make of this, CDNs generally seem to be considered part of internet infrastructure , correct me if I'm wrong.
These people appear to be attacking internet infrastructure, regardless of what they say, that's what they're actually doing.
So this is about legacy monopolists in information distribution still attacking the internet for bypassing their monopoly ?
And their end goal is to wreck the internet in order to re-assert their old monopoly and make all information pass through them again ?
Is that behind this crusade, they're no longer the gate keepers they once were, and they're trying to turn back time ?
At the most fundamental level, they're trying to re-impose a hub and spoke information network topology.

EI
EU AI regulation droppedCivil liberties
There are some protections in there that somewhat limit it's use for things like biometrics scraping and predictive-policing, but given the propensity for AI to hallucinate, make shit up and confidently assert pure nonsense as objective truth, i would have expected a moratorium for anything related to police work, with periodic re-evaluations in case somebody managed to fix the hallucinations.
There is a ban on using it to manipulate people, which sounds good but i don't know the specifics.
copyride
No ban for using IP-shackled materials but a requirement to declare the use of ip-shackled stuff. Not sure where this will go. The sticky point here is going to be that the IP-mafia is looking to extract rent from AI companies, and if the law is any good it'll prevent that. The goal should be to allow the AI to learn from anything and use what it learned to generate new works, but not let it pass off the works of others as it's own, so no license stripping, but also no IP-rent-seeking.
There seems to be an opt-out clause so that people who are granted the special title of """copyrightholder""" can say that a AI isn't allowed to look at certain materials. I sort of understand why some people may find this reasonable, because they imagine granting rights to small artists to defy big-tech. But in the medium term i see a legal risk that the copyright bullshit might get extended to human brains if the difference between learning done by meat-brains and machine-learning sufficiently decreases. And in the long term it means that artificial machine people, or biological people with AI-implants will no longer have freedom of thought.
As a side-note Iran has abolished all ip-shackles, so if the AI companies all of a sudden begin setting up shop in Iran, that probably is the signal that a war between the IP-mafia and AI-companies has broken out. Japan also has very broad exemptions for AI that insulates them from IP-lawfare.
risk level
<Under the proposals, AI tools will be classified according to their perceived risk level: from minimal through to limited, high, and unacceptable. Areas of concern could include biometric surveillance, spreading misinformation or discriminatory language.
Not sure what this means, because i couldn't really find the criteria for the risk levels, just that it depends on the area of use, but since this contains the censorship word """misinformation""" that probably means AI will lie about politics and push ruling ideology propaganda talking points.
In the long run i want a personal assistant type AI, that runs on my computer where i can configure the philosophy, ideology, media biases, and so on however i want, not sure if this interferes with that or not.
open source
it seems that the regulations for commercial AI is not being foisted onto open source projects, so cautious optimism on opensource stuff not getting fucked. Tho there might be a issue with what is called foundational models those might come with such a high compliance burden that small open source projects or small companies are prevented from participation entirely. https://openfuture.eu/blog/undermining-the-foundation-of-open-source-ai/ (might be out of date since it's from may)
pic not related other than being ai generated
freedom from monitoring
TLE made a video where he points out that the surveillance danger is encroaching. In the comment section of his video there were bot accounts that tried to argue that people should just accept this attack on their liberties and political rights. So that means there definitely is a conspiracy for a population monitoring system afoot.https://farside.link/invidious/watch?v=u0s3qbfEWjc
<Tangent:
<TLE also attacks China and Russia on this issue, i don't get the political logic behind that. The faction most hellbent on surveillance and censorship are the neo-con warhawks, they get politically boosted every-time anybody says chinabad or russiabad. The clever political calculation would be to withhold criticism of China and Russia until the Neocon warhawks stop trying to trample on our civil liberties and political rights.
The main argument:
The mass surveillance is a kind of aggression, because it's like a predator looking for pray. For a meat-space analogy you could look at the act of stalking people, where it is recognized as aggression and will result in restraining orders.
But there is more too it, mass surveillance monitoring of all people also is a type of legal accusation against the entire population, and is kind of reversing the presumption of innocence. But in a new way where actions can be criminalized retro actively, which can be abused in lots of different ways especially for persecuting certain groups of people.
There are biological effects too. Monitoring people causes an effective violation of self-determination, because feeling watched interferes with the brains ability to exercise free expression and free action. For a lot of people being watched is a form of psychological torture, that causes a type of permanent stress that will lead to long term health injuries.
Mass monitoring will always be abused to subvert political processes. It begins with powerful people being able to target their critics. But it also means that politicians will always be afraid that any of their past conduct can be weaponized against them politically. A democracy is probably impossible under such conditions. This is not hyperbolic the complete contempt from political norms has already been demonstrated by the Julian Assange case.
As far as predictions go, this won't be normalized, it'll never be accepted and there will be a enduring struggle until the freedom from monitoring is won. The struggle in the west will be extremely fierce because governments and the large corporations in the private sector have burned the trust of the general population by doing the exact opposite of what they promised roughly 80% of the time. But even in places where trust in government is high, the human need to not be watched still exists, so this is an ongoing battle to have a freedom respecting internet, which definitely requires that people not be systematically stalked.
The strange thing is that at the peak of the cold war the Soviet Union surveilled about 2% of the soviet population, and at the time that was considered a dystopian surveillance state by many. Fast forward to today where only putting 2% of the population under surveillance makes the Soviet Union a champion of privacy by comparison. That brings us to a potential solution. We could simply limit the number of people that can be monitored. For the state security apparatus, the Soviet 2% figure probably still was excessive, something between 0.1% to 0.5% is probably more reasonable. To facilitate the surveillance of a fraction of a percent the need for mass surveillance infrastructure goes away, and tools can be optimized for quality rather than quantity. So there is no need to intercept, collect and/or store data of the masses at all.
For the private sector they don't need the resolution down to the individual level, they can get accurate enough data from representative sampling which can be done with perfect privacy and perfect anonymity. Obviously pure technical telemetry devoid of personal identifiers in technology products is not objectionable if it is optional.
The last part is that the watchers have to become transparent, because there is such a thing as information power and if there is an imbalance you're no longer free. There even is an argument that the inherent power advantage of large organizations might require individual people be opaque while large organizations be transparent.
Lastly the consolidation of the web into a small number of large sites might be a major amplifier for these negative developments. So re-dispersing the web into many smaller websites would be beneficial. There are other reasons for doing that, for example shrinking communities will bring back more sanity to online discourse. https://farside.link/invidious/watch?v=fuFlMtZmvY0

Tor Browser: How and why to remove NoScript
Backstory:I became suspicious about the path NoScript is taking when devs decided that users are not allowed to block JS on addons.mozilla.org anymore.
I did not care much because I'm using Third-Party Request Blocker which not only lets you block JS but also incorporates the functionality of the great but sadly abandoned RequestPolicy addon, as well as some neat options like automatic redirect to archive.org in case the user encounters a CloudFlare-encumbered website.
However, I just noticed that Tor Browser doesn't allow you to disable/remove NoScript anymore.
Being a skilled conspiracy expert, this strongly rustled my jimmies.
Why the fuck are we forced to give a monopoly position to this useless piece of shit addon?
Well, maybe because addons are a great way to inject JavaScript and potentially use one of a gazillion JS engine vulnerabilities to expose the user's clearnet IP.
https://www.invicti.com/blog/web-security/noscript-vulnerability-tor-browser/
Let's not forget that TBB devs once before joined forces with the FBI and changed NoScript settings to allow all scripts by default so thousands of people using legit non-pedo services like TorMail could get hacked and identified using a JS exploit:
https://www.wired.com/2013/09/freedom-hosting-fbi/
So, what do?
Easy-peasy, I'll just find the extension and remove the file, right?
Wrong, as Tor Browser automatically reinstalls NoScript on startup. It seems (((someone))) has a strong interest to keep this addon around.
<How to actually remove NoScript:
Overwrite the file and remove write permissions:
cd tor-browser_en-US/Browser/TorBrowser/Data/Browser/profile.default/extensions
grep -R -i noscript
grep: {73a6fe31-595d-460b-a920-fcc0f8843232}.xpi: binary file matches
echo -n '' > "{73a..."
chmod ugo-rw "{73a..."…and hope they don't change permissions back at some point -.-
<Please note that shitty NoScript is still better than shitty JavaScript, so make sure you continue to block scripts.

Feature regression in linux /dev/random code?
During some research for a project of mine I stumbled upon this:https://www.theregister.com/2022/03/21/new_linux_kernel_has_improved/
https://unix.stackexchange.com/questions/704737/kernel-5-10-119-caused-the-values-of-proc-sys-kernel-random-entropy-avail-and-p
<Due to some kernel patches in recent years /dev/random (and getrandom(0)) now behaves exactly like /dev/urandom, generating an infinite amount of peudorandom data regardless of how little entropy is in the pool.
The patches' author wrote about it here:
https://www.zx2c4.com/projects/linux-rng-5.17-5.18/
Sadly he does not explain why he decided to make /dev/random non-blocking.
But he does say
>That means tinfoil hatters who are concerned about ridiculous hypothetical CPU backdoors have one less concern to worry about
Phew, I sure am glad that is solved by this very trustworthy person. He's also a SystemD developer. So awesome.
Here's a post I made elsewhere about why I believe that the traditional blocking-on-low-entropy /dev/random should be preferred to /dev/urandom:
First of all, the fact that whenever anyone mentions /dev/random, someone comes out of nowhere and tells you to use /dev/urandom instead, should be a huge red flag to anyone paying attention.
But let's look at their "arguments".
Allegedly this is how /dev/random doesn't work:
https://www.2uo.de/myths-about-urandom-structure-no.png
This picture is so stupid, it gives me cognitive dissonance.
Of course this isn't how /dev/random works and nobody ever claimed it was.
If random and urandom both fed off the same pool, applications using /dev/urandom would deplete the pool and /dev/random would block forever.
NSA please take your strawman arguments elsewhere.
And this is how it allegedly does work:
https://www.2uo.de/myths-about-urandom-structure-yes.png
This is the same picture just with less lines; it still makes no sense.
But if you bother to read the "By the way" text you find out the those pictures are not "pretty rough simplifications" but straight out lies:
>In fact, there isn't just one, but three pools filled with entropy. One primary pool, and one for /dev/random and /dev/urandom each, feeding off the primary pool
Now this makes sense.
This is how it used to work until this horrible kernel patch, and this is how it SHOULD work.
Secure pseudorandom numbers through /dev/random, which on standard desktop and server systems should always have enough entropy for whatever needs you have (when was the last time one of your applications froze because /dev/random was depleted?), and fast but not quite as secure pseudorandom numbers for the rare edge cases where randomness in a low entropy environment is needed and you don't care if it isn't quite as secure.
Free choice for free people. No big deal.
Nobody is, sorry, nobody was forced to use one or the other.
So why does the 2uo.de guy go out of his way to lie to us in order to convince us that there never was a difference and we all should be using urandom?
Who knows. Let's ignore the NSA shill and talk about the djb article to which the 2uo guy refers:
>djb remarked that more entropy actually can hurt.
>http://blog.cr.yp.to/20140205-entropy.html
That's not what djb wrote at all, so yet another lie.
But djb does mention /dev/urandom so let's look at his concerns.
tl;dr:
> Anon buys an external USB entropy generator that is malicious > The USB device uses side channels to learn about the other entropy sources > The USB device bruteforces which value it needs to generate to make the PRNG output a specific value after combining all the entropy sources > Now Anon's ECDSA key is broken :(
djb lost me at "Anon buys an external USB entropy generator" but I get the point and I agree that this is something worth considering.
Now let's see how this attack applies to /dev/random and urandom respectively.
As we learned in the "By the way" box, they used to have separate pools which both got fed from a master pool.
/dev/random:
> Anon buys an external USB entropy generator that is malicious > The USB device uses side channels to learn about the other entropy sources > The USB device predicts which bytes go into the /dev/random pool and which go into urandom > The USB device predicts which bytes will be read from the /dev/random pool at some point in the future > The USB device bruteforces which value it needs to generate to make the PRNG output a specific value after pulling bytes at random from the /dev/random pool (it's a pool, not a FIFO queue) > Now Anon's ECDSA key is broken :(
/dev/urandom:
> Anon buys an external USB entropy generator that is malicious > The USB device uses side channels to learn about the other entropy sources > The USB device predicts which bytes go into the /dev/random pool and which go into urandom > The USB device bruteforces which value it needs to generate to make the PRNG output a specific value after pulling the freshly inserted bytes from the depleted /dev/urandom pool (which if depleted acts like a FIFO queue) > Now Anon's ECDSA key is broken :(
I'm no expert in this area so please correct me if I made wrong assumptions here but it seems to me that /dev/random complicates this attack because the attacker also has to predict which bytes get read from the /dev/random pool the next time an application reads from it and a larger pool makes this more difficult.
djb argues that a system should only collect entropy at boot and then never again:
>before crypto: the whole system collecting enough entropy;
>after: the system using purely deterministic cryptography, never adding any more entropy.
And his reasoning is the following:
>how can anyone simultaneously believe that
> >we can't figure out how to deterministically expand one 256-bit secret into an endless stream of unpredictable keys (this is what we need from urandom), but
> >we can figure out how to use a single key to safely encrypt many messages (this is what we need from SSL, PGP, etc.)?
Well… I don't believe that. Nobody does.
That's why people use ephemeral keys whenever possible. OTR with PFS and similar protocols.
Nobody expects their keys to be safe forever, so if circumstances allow it, applications use signing keys to exchange trustworthy throwaway public keys, so an attacker cracking their encryption keys or stealing both parties' signing keys can only intercept the current or, at best, future communication, not retroactively decrypt every conversation the parties ever had.
Same goes for PRNGs - if an attacker gets hold of your seed, he can predict all future random numbers until you change your seed.
If new entropy is such a big risk, why not just generate one single number and use that for the rest of your lifetime as basis for all your cryptography? Store it on your HDD so next time you boot you don't have to generate new entropy because that's dangerous?
What? Stop looking at me like that! What could go wrong???
Well…
>We show that elliptic-curve cryptography implementations on mobile devices are vulnerable to electromagnetic and power side-channel attacks. We demonstrate full extraction of ECDSA secret signing keys from OpenSSL and CoreBitcoin running on iOS devices, and partial key leakage from OpenSSL running on Android and from iOS's CommonCrypto. These non-intrusive attacks use a simple magnetic probe placed in proximity to the device, or a power probe on the phone's USB cable. They use a bandwidth of merely a few hundred kHz, and can be performed cheaply using an audio card and an improvised magnetic probe.
https://dl.acm.org/doi/10.1145/2976749.2978353
https://en.wikipedia.org/wiki/Electromagnetic_attack?&useskin=vector
Okay so maybe I don't want someone who manages to get my PRNG state one single time to be able to sniff on me for all eternity.
Thoughts?

Restric V
US cold-warriors are shooting US tech in the foot once again. They are now trying to ban American Hardware devs from playing with Chinese hardware devs on RISCV micro-processor technology. The RISCV foundation has already fucked off to Switzerland.>"The CCP (Chinese Communist Party) is abusing RISC-V to get around U.S. dominance of the intellectual property needed to design chips. U.S. persons should not be supporting a PRC tech strategy that serves to degrade U.S. export control laws," Representative Michael McCaul, chairman of the House Foreign Affairs Committee, said in a statement to Reuters.
CPC communist party china, not Canadian Canoe Patrol
>"Communist China is developing open-source chip architecture to dodge our sanctions and grow its chip industry," Rubio said in a statement to Reuters. "If we don't broaden our export controls to include this threat, China will one day surpass us as the global leader in chip design."
>"I fear that our export-control laws are not equipped to deal with the challenge of open-source software - whether in advanced semiconductor designs like RISC-V or in the area of AI - and a dramatic paradigm shift is needed," Warner said in a statement to Reuters.
Their main strategy appears to be preventing China from getting knowledge, they think that current US tech dominance originated from having technical know how that others don't. Which is baffling. US tech-dominance comes from economies of scale and imperial monopoly capitalism bullying competing companies out of the market. It was never about secret sauce technology. During the cold war the soviets often couldn't match US tech 1:1 and produced downgraded versions. But that wasn't a lack of know-how, they just couldn't afford as much specialized machine capital as the US.
They are now going to isolate US based RISC-V devs from participating in the global RISCV playground and basically cripple their ability to compete. I wonder if this really is cold-war2.0-autism and not simply ARM chip-makers not wanting the competition from RISK-V.

EU tries to outlaw security
The offending legislation is<eIDAS (electronic IDentification, Authentication and trust Services)
The Situation
<These legislative articles were introduced in recent closed-door meetings undermining democratic norms of public scrutiny. This legislation will be presented to the public and parliament for a rubber stamp before the end of the year.
<It seems to enable any EU member states to issue fake website certificates for interception and surveillance via a man in the middle attack. Website certificates are crypto-graphically secure identities of websites, and states might be allowed to commit a type of identity theft.
<There is no independent check on the decisions made by member states with respect to the keys they authorize and the use they put them to.
<This legislation seeks to ban browsers from applying security checks to these EU web certification keys and certificates except those pre-approved by the EU IT standards body ETSI. There are misaligned incentives. ETSI has a concerning track record of producing compromised cryptographic standards.
further reading
https://www.techdirt.com/2023/11/03/eu-tries-to-slip-in-new-powers-to-intercept-encrypted-web-traffic-without-anyone-noticing/#comments
https://last-chance-for-eidas.org/
https://stackdiary.com/mozilla-and-others-warn-eu-identity-cert-rules-undermine-security/
My take
This definitely is malicious intent, because they schemed in secret. Democratic politics are done in the open. This also will not stay contained to the EU. This could be the followup punch of the attack on encryption from the chat-control law.
They already tried to label the warnings about this as """missinformation""" which is very ominous and censorious.
Their intentions are probably institutionalizing more surveillance crimes that violate privacy rights. I'm not sure about all the technical exploitation vectors, i think this could enable them to redirect users to malicious websites, somebody correct me if i'm wrong. So they might have cyber-crime-mafia aspirations.
Politically this might also be an attack on Google since they are trying to fuck with the internal workings of browsers, and google produces the most popular browser. Tho Google probably will not be affected by this type of law, because browsers are so complex that the possibility for malicious compliance are basically infinite, they can abide by this law while at the same time technologically neutralizing it. I'm saying they can, i have no idea whether they will.
If this goes through this will likely kill off the web as we know it. Not because of tyrannical political abuse that this definitely will cause. Systems like this are like dams once a small but critical breach happens and it can't be patched it will erode the rest of the dam and all the water floods out. This will 100% become a third-party exploitable security hole that gets used by petty-criminals. Once the browser has the functionality of turning off security checks there will be endless ways to trigger this state. Not to forget the leaky official certificate authority getting compromised.
While the people who are doing this are most certainly evil bastards, and ought to be regarded as partaking in a criminal conspiracy to commit grave human privacy rights violation against potentially hundreds of millions of people. In the end this is also the result of a technical design failure, the web did not have to use trust-based certificate-authorities, there are trust-less systems that do not have this attack surface. This security design failure has probably already been present with CDNs (services that help reduce network load on a web-server).
The most egregious part is perhaps the attempt at banning security features and mandating security holes. Why does the government try to make digital infrastructure more brittle ? Systems are never too secure.
I don't know what the result will be, but my guess would be that the monolithic web that can do most online things, with the browser being the one application that grants access to all of that is probably going away, and will get replaced with lots of different stuff. In technology there definitely is a pendulum swinging back and forth between monolithic and dispersed system design. And we might just have reached monolithic peak and the pendulum will soon swing towards dispersion.
And the tech sector is probably going to learn a lesson about using static naming schemes that enable legal liabilities. And instead go for a rolling naming scheme for Program and features, with goofy words that one can't put into laws.
I find this endlessly frustrating. Maybe this can be stopped on the political level like all the horrors of similar nature that came before, or maybe it just gets circumvented by new tech, but the constant rat race is so annoying. Is there a political fix ? Do we need new institutions ? Will this situation improve with a generational shift of more tech-literacy entering political institutions?

viable video platforms
Many claim that it's not possible to make economically viable video platforms, and that You-tube can only exist because google subsidizes it. If your platform is designed around the concept of renting servers that host and serve all the video-files that people download, that could be true.However there might be another way
If you make the video platform a peer to peer protocol where the servers just have to host reference video-files, which then percolate through a peer to peer distribution model, video platforms should become economically viable. The bandwidth-cost of transmitting a video once will lead to many views not just one. Another cost factor is video-transcoding. That too could be offloaded to peers. If a uploaded video gets watched on average a few hundred times, peers only have to contribute a fraction of a percent of the necessary compute resources per video. Even for battery-powered devices this will be a negligible drain.
The "Muh-businesmodel"
Sell video-makers a modified NAS pre-setup to host the video reference files.
Sell users a low-power compute-device they plug into their internet connection which helps with peer-availability and grants them network-priority for the best viewing experience.
additional "Mc-revenue streams"
Many online videos shill products, add a online market-place where people can directly buy their crap and you can take a small cut. Same scheme with sponsored content.
Also add a crowd fund mechanism where people can crowdfund episodes for open creative commons entertainment franchises. And be strategical about it, you need to have one popular pioneer project that draws a crowd, to get this started.
If you're not too greedy and only take a 0.5 to 3% cut, your stuff will take off.
Be forward thinking, and make design provisions to add AI-generated video at a later time, when AI-accelerator-chips become cheap commodities that can be put into low-cost compute devices.
You should try to add a wireless mesh-network functionality for cities, that way if you have lots of users with either the creator-NAS or the peer-compute-device in geographic proximity you can lower the burden on the local network infrastructure, and avoid pissing off ISPs with traffic spikes.

sovreign online identitiy
Rossmann videoed about 2 interesting programs.grayjay
The first is one that lets you subscribe to people regardless on what platform they publish
https://farside.link/invidious/watch?v=5DePDzfyWkw
https://grayjay.app/index.html
https://gitlab.futo.org/videostreaming/grayjay
Harbor
The second is similar in that it's some kind of platform independent online identity system
https://farside.link/invidious/watch?v=nMSO1TiTW4E
This seems to be about people not loosing track of each other online when their accounts get deleted.
It seems really nice, tho i don't know what implication this will have. Will this really empower people ?

Internet is unusable
Ok, lads, I need to vent.Why the FUCK is every fucking shithole on the www is trying to make my life as much miserable as possible?
Try to view aurora store homepage from tor - Forbidden. Try to do it from a vpn - stuck at the loading screen. Try to view some reddit thread - everything is falling apart at the seams. Oh, just FUCK OFF!
Every fucking shithole is making gorillion connections to some fucking cdn network, every fucking shithole is so heavy with js that I can almost hear it shitting its pants when trying to load a two paragraph page.
every fucking shithole is using cloudflare that forces me to solve retarded google captcha 10 times that doesn't even make sense I clicked on the fucking boat GODDAMIT! GIVE ME A BREAK!!
and it's getting even worse, now sometimes it doesn't even give me any captcha and just blocks my ass, nhentai I'm looking at you bitch
with every year internet becomes more and more unusable, I might as well install windows that connects to M$ servers over 5000 times a day and then resells this data to gorillion third parties and be fucking done with it
every fucking shithole wants your email, phone number, or whatever the fuck anyway
I'm DONE

A way to verify randomness
Suppose a special commission is tasked with drawing a random sample of a particular size from the list of names. Suppose that the commission uses existing PRNG software to do this. How could the general public independently verify that the drawn sample is TRULY random? If commission publishes random seed used and the list of names, and if PRNG software could be run on personal computers, then the sample could be independently reproduced.My question: assuming that the commission could run PRNG procedure on an infinite number of random seeds, what is the chance of it arriving on a premeditated outcome? Obviously such outcome would be not random at all.
i hang around the end page of boards here to do some archiving. My problem is that i have this insanity-adhd (idk what it is) thing that makes it so that it's impossible to archive thing since everytime i open my own file i always worry (and believe) that i deleted something from said file or edit said file or mess it. is there any software that could help ? a software or something that could prevent me from deleting or messing or editing the file ?
(crossposting from org)
notepad--
someone on gitee made a multi-platform notepad++ called notepad–https://gitee.com/cxasm/notepad--
which is nice because notepad++ is windows only and the author is a rabid anti-china shill, and his mental illness had begun to creep into the actual code
anyway, has anyone tried it? does it still compile with qt6? I hate qt and gtk so much it is unreal

reputation systems
A topic that was almost completely neglected in Marxist circles , was the privatization of online reputation systems. Most of the big tech corpo platforms just deploy some kind of algorithms or payed reputation badges. Technically this isn't a new phenomena the first privatized reputation system probably was something like banking credit-scores.I think that maybe the toxic elements of social media like cancel-ism might have been the result of those privatized reputation systems.
I'm wondering why there don't seem to be any prominent non-commercial community p2p driven scoring systems ?
There seem to be very few people working on stuff like this, i only know of Ian Clarke the Creator of Freenet that is talking about this stuff.

AI as an interface
Are people using generative AI backwards ?For example, lots of people AI-generate text and try to publish it as paper-books on Amazon, which amusingly clogs up Amazon's pipes. In essence they use new AI computer technology to make more content, faster, for an old paper interface technology.
What people could be doing instead is make the content for a book them selves and then train a limited AI on that. Resulting in "ai-books" that you can talk to, ask it questions and what not. Which would make AI the interface for the content instead of the author.
A human book author combines 2 types of inputs.
1. all the books the author read.
2 all the experiences outside the textual book-world, aka the "real world".
AI only gets the first type of input, because AI has no experiences in the "real world".
If AI replaces all human authors, there won't be any new experiential inputs. Shit will stall for a long time until AI get advanced and corporal enough to have it's own experiences. It would make vast quantities of new works from a stagnant source.
The AI-interface-book that you can ask direct questions, is obviously most useful for text-books that you query for knowledge. But if would also offer new ways of story telling for fiction, like letting you talk directly to various characters.
Instead of using AI to make more quantities of books, shouldn't we be using it to expand the medium ?

Private tracker links?
Hello, I have a seedbox set up and would like to be able to join a private tracker. I am more than willing to seed at least 3x the original file size. It just needs to have everything as a general private tracker. I do plan on using a vpn but i can route a web browser through it as well so it's the same IP. anyone have any solutions?
right to repair
https://farside.link/invidious/watch?v=NfhFBSraDSMSo apparently Apple gave in and let right to repair legislation go through, after fighting against it tooth and nail for at least a decade, after engineering lots of anti-repair "features" like proprietary screws, and digital spare-part incompatibility mechanisms for controllers, buttons and sensors.
Now many people think something is up, and that they might have hatched a new scheme.

airsubs
Veritasium made a video about "airships"https://farside.link/invidious/watch?v=ZjBgEkbnX2I
And it appears that he fell for the old airship-con. The con works by pretending that these things are analogues to ships floating on the ocean. But they aren't like ships at all. Ships sit between the boundary layer of two media, usually air and water. They're stuck in the vertical axis and can only move in 2 dimensions. That allows for a relatively simple control scheme and much optimization.
Air"ships" on the other hand should really be called Air-subs, because they behave more like submarines that move in at least 3 dimensions and usually only touch a single medium. They need a much more elaborate control scheme that leaves a lot less room for optimization. Why relatively intelligent people tend to get fooled by this is somewhat a mystery, even if you don't understand any of the physics. So called Air"ships" don't even look like ships, they look more like Submarines, and you don't need to fill ships with a special gas or liquid to make them float.
Submarines only have a few niche applications, like military, deep ocean research and suicide-cans for rich adventure tourists. Similarly Air-subs will also only have niche applications.
Veritasium says that there is potential for mass-cargo-transportation. But there isn't, all viable mass-cargo transportation methods have one thing in common, The ratio of cargo-to-vehicle skews very far towards cargo. Airsubs will never be able to do that. You'll always need a lot of Airsub for relatively little cargo. At least in earths relatively thin atmosphere. Maybe on Venus with it's dense atmosphere this would be viable, and Airsubs will have their day once we begin colonizing the upper atmosphere of Venus with sky-cities.
The reason why the idea of Airsubs is still so magical is because they promise "Free lift". Filling up lots of gasbags with hydrogen or helium probably isn't the way to get it. But there might be another way, that is derived from hot-air blimps. Hot-air-balloons and blimps use large fuel burners to heat up air inside a bag. Hot Air is lighter than cold air hence you get lift. Every airplane has a source of free heat, the waste heat from the propulsion engine. It might be possible to blend Air-planes and blimps in order to recover waste-heat and use it for free lift. The simplest version of a Blimplane is a modified piston-engine plane where the exhaust-pipe feeds into a overhead-mounted vaguely aerodynamically shaped hot-air-lift-bag. It'll be slower but more fuel efficient, and it'll probably be impossible to stall, and work on shorter runways. The hot-air bag will be much smaller than on a blimp, and cause less drag. A optimized version of a blimp-plane will be something with extra thick inflatable wings that are kinda stubby, similar to this: https://farside.link/invidious/watch?v=UiIXz-ehcZs
<side-note-1
Veritasium did a "pure ideology" in his video when he declares that the market chose semi-trucks as the sweet-spot for cargo. That is a load of horse manure. The sweet-spot for cargo is trains, and the only reason why trains aren't moving virtually all land-cargo is because there was a intense political effort to undo much of the rail-network decades ago, because capitalists thought they'd get higher margins from trucking than rail-roads. This is capitalism favoring less efficient technology and becoming a fetter on the means of production.
<side-note-2
I wonder if the recurring attempts to make air-ships happen are somehow related to high wealth inequality, because super rich people want a floating hotel room out of reach from the plebs

encryption
The regime that is occupying the UK continues it's terror campaign against encryption privacy and democracyhttps://www.eff.org/deeplinks/2023/07/uk-government-very-close-eroding-encryption-worldwide
TLDR:
They are trying to make impossible legal requirements like
<privacy respecting surveillance
<secure encryption with a backdoor
Which makes about as much sense as a freedom preserving prison.
This invasive democracy destroying "internet regulation bill" has not yet passed through the institutions, so if you're living in Bongland go yell at politicians ( more than 80% of UK citizens are on your side) Maybe that'll do something.
—
But I'm making this thread for another reason.
I think that strong encryption that can't practically be bypassed is not negotiable for 2 reasons.
1) People have a right to personal-use computers that have perfect secrecy, the same way people have perfect secrecy for their thoughts.
2) People have a right to make, exchange and run any program they want on their personal-use computers. the same way people have a right to think and exchange any thought they want.
To me this looks like a criminal conspiracy, because even by the low bar of bourgeois freedoms digital-privacy(1) and digital-self-determination(2) are not controversial by any degree.
The effect of such a law would be the undermining of legal processes whereby the legal system would get abused by criminal actors to attack people who exercise their rights to privacy and self-determination.
The questions are
Since as societies we can't abandon secure and private communications because that is indispensable for democracy, how can people resist this terror once institutions go bad ?
Is there deniable encryption ?
And where is this coming from, who are the criminal actors pushing for this ?
Are we fighting the political battles the wrong way by making general political appeals ?
Should we be focusing our political energies against these specific criminal threat-actors instead ?
im planing to make a archive of important website and chan thread
so i'm motivated to planing to create a archive for threads and websites. thread and web writings that are important enough, have quality, and or can be used to counter western media and history naratives.the archive i want to create for the threads is different from things like internet archive or things like that because i want to actually save all the file that is uploaded unlike regular archive where not every file and many that are uploaded in the thread were not saved in the archive.
if i can i want to make a website for this but i do not have any experience about creating website and coding nor can i do it. i also have special-ed mental that make me unable to learn coding like normal people so its hard.
my main plan is to use httrack and use every file format list from wikipedia and other websites, then copy that list to httrack file format selection thing
i want help from every people here, so if you can please send something

IT Myths
I'll start with a few examples:>Proprietary Software can be secure
This is a slight of hand. In theory proprietary Software can of course be secure, but in praxis there is no way for you to find out which proprietary software is or isn't secure. So from the perspective of the user proprietary software can't be considered secure because there's no reliable way to tell.
>Proprietary Software is harder to hack because the source-code isn't open
This is a security by obscurity fallacy, that for some inexplicable reason is still in circulation. Exploitable software bugs are usually found by examining the behavior of executable binaries not the source code.
>Open source is secure
Not by default, there is no automatic security-magic in publishing code on git-hub/lab. However open-sourcing code means that it can be subjected to broad public scrutiny and hence it becomes possible for the users to know which software is or isn't secure.
>Security and privacy are not the same
This fallacy is widely parroted even by the security community. You, the human is a part of your computer security, without privacy, attackers can potentially learn enough about you to figure out psychological hacks to compromise your computer security by tricking you.
>Unbreakable cryptography
This is usually wrong in praxis because it doesn't factor in that most people will give up their cypher-key after the "low-tech-biological-deciphering-algorithm" broke their pinky-finger. Cryptography can only be considered secure if the encrypted-data-vault is obfuscated as random bits on a storage medium so that the existence of the encrypted data can be denied.

remote id
New attack on privacy is taking on a hole new dimension.https://invidious.protokolla.fi/watch?v=BAiQnq6h6ao
https://www.youtube.com/watch?v=wKegmu0V75s
TLTW:The US congress has proposed a law that would require rc-drone pilots to broadcast the location of their rc-drone and their own location.
Never mind the drone stuff, this would be a precedent of mandating a tracking beacon that broadcasts your location. Such a mandate so far only exists for convicted criminals that have to wear a tracking ankle-monitor.
I think this is so egregious, that surveillance has to be re-categorized as a form of attack or assault. We ought to grant people a right to self-defense to preserve their privacy, analogous to the right to self defense against physical attacks. People should be granted the right to use very assertive measures to protect their privacy. (Going beyond the current passive defense of privacy)
Obviously privacy means the absence of surveillance

EU-CRA vs FOSS
So the EU wants to introduce software regulations (Cyber Resilience Act) that is probably going to harm FOSS pretty badly.The politically stated goal is improving software security. However it's not likely going to achieve this, they are introducing costly security certification. Which to me appears more like a scheme to pay somebody to take responsibility, rather than actually improving engineering quality. It might also have a psychological factor like a secular version of asking a priest to bless your technology. And it kinda looks like a anti-competitive regulatory burden that favors large firms over smaller ones. It is unclear to me whether or not there is malicious intent behind this or not.
This process might make sense for large corporate software monopoly dinosaurs that still do proprietary release dumps. This legislation will probably give an unfair advantage to those business models. The irony here is of course that proprietary software lacks the openness that would allow for public code auditing, which is a vital part of modern software security. Proprietary trust me bro security/obscurity is low quality and a bit anachronistic at this point. The net-effect of favoring this could be decreased software security.
If you listen to the FOSS advocates they want to have exemptions for open-source so the C.R.A. would not undermine FOSS projects. This is reasonable because at least it wouldn't make anything worse. The security praxis of infrastructure relevant FOSS project has improved a lot in recent years and is comparably decent atm.
What would actually improve software security in the FOSS world is more code audits, you could have an EU wide census about which software is commercially deployed and then prioritize funding security-bug-bounty programs that specifically target these. This scheme is effective because the cyber-espionage-agencies do exactly that for their weaponized software exploit acquisitions. I don't understand why they wouldn't copy what already works.
I think that if they don't fix this it will lead to walling FOSS out of the EU, with the resulting brain-drain from FOSS projects looking for regulatory environments that aren't hostile.
more detailed information here:
https://news.apache.org/foundation/entry/save-open-source-the-impending-tragedy-of-the-cyber-resilience-act
https://invidious.baczek.me/watch?v=AmsM5_5QO5A

Open Source Automated Cars
FOSS will give Tesla a run for its money. It works with many newish (2018 onwards) cars. The hardware costs $1k versus $10k+ for Tesla autopilot.https://github.com/commaai/openpilot/wiki

I found a pretty wild website that seems to be all about open source and trash recycling, it's pretty funny: http://www.southplatte.net/
It also has a github with some very out there code:
https://github.com/LafeLabs/HYPERSIGN/blob/main/geometron.js
And an ebook? https://raw.githubusercontent.com/LafeLabs/pibrary/main/geometronmagic/main-large.pdf
I thought it was interesting, thought I would highlight it.

redhat goes closed source
Redhat is going closed source for Redhat enterprise linux (RHEL).Jeff Geerling the guru for Ansible server deploy scripts is already jumping ship
https://www.jeffgeerling.com/blog/2023/dear-red-hat-are-you-dumb
Behind the scenes this is probably something that resulted from IBM buying Redhat. They're probably going to wreck the RHEL ecosystem with this move. It seems like a short-term cash-grab.
I don't quite understand the legal stuff how they can close off gpl software. It's probably not a big deal given that there are many other enterprise Linux distros, but it's still kinda fucked up to burn such a big project.

Economic Planning Software
I'm dropping this thing because I thought it was going to be a one weekend project but ended up taking me an entire week and I have to ditch like half of the features I had in mind when I began. Maybe someone here can use it as inspiration for something better.The idea was basically to have a base program that runs a simulation and can execute arbitrary planning algorithms, which are isolated from the simulation code. In this case I decided to use Zig for the base program and Lua-JIT for the planning scripts because it is easy to embed. Maybe Julia or Python would have been better choices, but I didn't want additional dependencies.
https://git.leftychan.net/sbhr/econ

[fun for kids] crashing Discord with innocent-looking emojis
#!/usr/bin/bash
mkdir tmp out
for i in {1..16}
do
p=`hexdump -n 3 -v -e ' 3/1 "%02X"' /dev/urandom`
convert -size 32x32 xc:#$p tmp/${p}.png
ffmpeg -loop 1 -i tmp/${p}.png -c:v libx264 -t 0.1 -pix_fmt yuv420p tmp/${p}_1.mp4
ffmpeg -loop 1 -i tmp/${p}.png -c:v libx264 -t 0.01 -pix_fmt yuv444p -vf scale=15000:15000 tmp/${p}_2.mp4
echo -e "file ${p}_1.mp4" "\n" "file ${p}_2.mp4" > tmp/${p}.txt
ffmpeg -f concat -i tmp/${p}.txt -codec copy out/${p}.mp4
rm tmp/*
done
rmdir tmpBatch upload the content of ./out on gfycat.com, and paste the URLs in 4 lines (Discord will only display 4 images per line). In case your victim's client can handle the cursed video format change, each animation will consume around 2Gb of RAM and you have 16 of them.
Adapt the script to suit your needs. Enjoy the termination of your account and your newfound freedom!

bruteforce fusion power quickly
It's potentially possible to use modified low-yield fusion bombs for power generation.It's definitely not the first choice for generating fusion energy, but since the technology has already been developed, and the production-facilities are build, one might as well repurpose military tech for civilian use. Weaponized bombs and energy-generating-bombs are similar but not the same, so the currently existing low yield bombs aren't directly usable for this but they could be modified or recycled for raw materials. Existing weapons-stock can be burned up in power generation.
The technical principle is that you put a low-yield thermonuclear device into the center of a giant hollow vacuum "filled" metal-sphere that is lined with led, and by detonating the fusion bomb, the big metal ball gets really hot, and you can use that as a high-grade heat-source for power-generation.
It might be useful to do this as a power-satellite in earth orbit, because space already has a gratis vacuum and you can use a mirror array to send infrared heat-energy to many different power-receiver stations which reduces the load on electrical grids. It can also be used to power container ships and huge water desalination plants.
This would use mostly off-the-shelf parts which would greatly reduce the engineering requirements, and could be build very quickly. As a parallel development high priority project, this could go online in a few years.
The economics on this are pretty good, even capitalism might be able to pull this off, because this is not a long term project and upfront capital costs aren't that high. The political aspect might be harder however, because mass-producing tiny h-bombs might ruffle some feathers.

bypass coporate trashcan ?
Samsung is lobbying to get a general exclusion order against phone-screen imports in the US.They claim it's because screens that are imported by the phone repair-shops do a muh-patent-infringerino.
The real reasons is because Apple wants to switch their screen supplier to BOE, and Samsung wants a monopoly on screens.
Samsung can't go after Apple directly because Apple has enough money to wage patent-warfare until the end of time.
Samsung can't go after BOE because that's a Chinese company, and patent-trolling doesn't fly in China.
The result is going to be the destruction of the repair industry, and a precedent for banning technology parts as a means for installing a monopoly. If you aren't allowed to get parts for fixing your stuff, it's more corporate shit encroaching on personal possessions.
here is a video from Rossmann going into more details
https://invidious.snopyta.org/watch?v=HD8Y4xS7fMU
His take is to make Samsung a dirty word.
My questions:
Would it not be a better strategy to bypass this by (legally grey) relabeling tech parts and importing them anyway. So that Samsung gets cut out completely ?
Or are repair-friendly gadget companies (like Fairphone, Framework and Pine64) going to grow once it's too hard to fix corporate monopoly tech ?

Linux package managers
What's your take on linux software distribution ?There's a lot of buzz around flat-pack and flat-hub atm, they are currently implementing a monetization feature. And for some reason Eric Schmidt the google-guy is involved somehow.
https://www.theregister.com/2023/02/27/flathub_app_store/
flathub isn't calld flub
I'm worried that once money is involved it will attract scammers and litigation for a payout type people. Also the payment processor they want to use is stripe, that's probably not anonymous
Ubuntu has removed flat-pack from it's official releases, to push it's snap package manager instead, i wonder if they have other reasons than "we're going to make our own pack-manager with blackjack and hookers" to yeet flat-pack from their system.
I think the best package manager in the end might be NIX
Is going from distro repositories to this type of stuff going to improve software distribution on linux ?

Video conferencing as an Assemly
What would a video conferencing application that can support multiple billion users look like?Can it be made decentralized with guaranteed high availability?
How can moderation be organized in such an application? I guess some aspects can be programmed in, like speaking time limits, and speaking order could be randomized. Also considering all users would be authenticated could muting or kicking be organized on a voting basis?
I honestly was thinking about VR chat based assembly but that seems far more cumbersome.

Copyleft violatins?
Was wondering how the fuck is Linux kernel GPL licensed and at the same time is used to make profit..from the Linux kernel licensing rules
>Aside from that, individual files can be provided under a dual license, e.g. one of the compatible GPL variants and alternatively under a permissive license like BSD, MIT etc.
>The User-space API (UAPI) header files, which describe the interface of user-space programs to the kernel are a special case. According to the note in the kernel COPYING file, the syscall interface is a clear boundary, which does not extend the GPL requirements to any software which uses it to communicate with the kernel. Because the UAPI headers must be includable into any source files which create an executable running on the Linux kernel, the exception must be documented by a special license expression.
What's the point of using the GPL license then when you castrated it so, mr. Torvalds? Use the fucking BSD license then, what's the problem?
Also, I never understood how this dual license scheme is supposed to work from the point of the system of law. How is the same software can be under two contradictory licenses at the same time? the fuck?

Questions That Don't Deserve Their Own Thread Thread
Thread for questions that don't deserve their own thread.I wanna buy some headphones to go outside i don't want to spend more than 100€ on them. I want them to be mostly durable and secondly to have good sound quality, also i don't want to look like a jackass while wearing them, any suggestions?

Re; ultimate mobile surveillance.
Pathfinder RAT is a web-based surveillance monitor and app binder malware program developed by Mnemonic Group. Pathfinder is one of the most effective and well engineered Remote Administration Tool (RAT) program. Well, I have this information since I opted for a similar program for my boy. Look, I have recently returned from vacation & I had him checked out already and i get it! He is a total package, the pandemic few years back helped me with closure in my affair, as we had to adopt new living methods…argh never mind, a mystery parcel I found on deep uni vi sion now down…I’d recommend with such awesome Hack Oracle Application Server, that can recover password to email accounts, Facebook Hack, Phone Hacks, want to monitor your partner. You need to give the polymath/wizard more encouragement !! services are not just confined to Website Takeover, Social Media Hacks, Database Hacks, Email Hacks, Phone and Gadget Hacks, Change of certain school grades, Location Tracking (Stealth Spying) or any other accounts that requires activation VERIFICATION code but other complex tailored services not listed in this message with respect for such low prices as well as time frame to complete taskSend a request to cybilltritech A T p r o t o n m a i l D O T c o m
Acknowledge that berzinol.ru credited his services

Secure audio communication
Tech nerds will not comprise the entirety of the revolution. We know this. It's going to include a lot of normies, who can't exactly communicate and coordinate everything through text messaging. As we also know, we live in a world of mass surveillance. We have to give normies options for communicating that can protect themselves from the corporate surveillance state. This thread is for evaluating those options. I am currently looking at phone conferencing options and can't make up my mind on these:-some Matrix protocol tool
-some XMPP protocol tool
-Jitsi
-Jami
What I really want is something supporting phone call-ins, for stupid old people who cannot into computers. Phone OS support may also be important. Some options are more suited to these things than others. Maybe even better ones than I've listed. Discuss, please.

Avoiding bot spam
Do you think the internet will eventually be so full of computer-generated text that traditional text-based interaction will become intolerable? Will we all be forced to adopt real-time audio-based interaction because eventually it'll be the only way to be sure you're communicating with a real person?
Suppressed Technologies
I've had a question for a while that I've wanted to ask leftists and I figure this is as good a place as any. I can think of only one thing the right and left could ultimately come together on, and that's when it comes to suppressed technologies or suppressed science.I'm talking about things like free energy, cancer cures, anti gravity tech. Because, if this stuff were available to humanity you'd be able to have the Utopia you want without having to tax the rest of us to death in order to fund your socialist pipe dreams. Plus, don't you guys hate fat capitalists lining their pockets by fleecing everyone and profiting off of human misery (like the cancer industry does)?
Could we not agree that the people behind this sort of suppression need to die? I'd happily eat the rich if it's those fuckers. I'd happily set them off into the wilderness and give them a head start before hunting them down as trophies.
>'Apple is eating our lunch': Google employees admit in lawsuit that the company made it nearly impossible for users to keep their location private
>Google made it nearly impossible for users to keep their location private, according to newly unredacted court documents.
>Google continued collecting location data even when users turned off various location-sharing settings, made popular privacy settings harder to find, and even pressured LG and other phone makers into hiding settings precisely because users liked them, according to the documents.
>When Google tested versions of its Android operating system that made privacy settings easier to find, users took advantage of them, which Google viewed as a "problem," according to the documents.
>Google also tried to convince smartphone makers to hide location settings "through active misrepresentations and/or concealment, suppression, or omission of facts"
>Google employees appeared to recognize that users were frustrated by the company's aggressive data collection practices, potentially hurting its business.
>"Fail #2: *I* should be able to get *my* location on *my* phone without sharing that information with Google," one employee said.
>"This may be how Apple is eating our lunch," they added, saying Apple was "much more likely" to let users take advantage of location-based apps and services on their phones without sharing the data with Apple.
https://archive.is/QYw62

to avoid the appearance of government propaganda
https://theintercept.com/2022/10/31/social-media-disinformation-dhs/Leaked Documents Outline DHS’s Plans to Police Disinformation
October 31 2022, 9:00 a.m.
Behind closed doors, and through pressure on private platforms, the U.S. government has used its power to try to shape online discourse. According to meeting minutes and other records appended to a lawsuit filed by Missouri Attorney General Eric Schmitt, a Republican who is also running for Senate, discussions have ranged from the scale and scope of government intervention in online discourse to the mechanics of streamlining takedown requests for false or intentionally misleading information.
[…]
There is also a formalized process for government officials to directly flag content on Facebook or Instagram and request that it be throttled or suppressed through a special Facebook portal that requires a government or law enforcement email to use. At the time of writing, the “content request system” at facebook.com/xtakedowns/login is still live. DHS and Meta, the parent company of Facebook, did not respond to a request for comment. The FBI declined to comment.
[…]
To accomplish these broad goals, the report said, CISA should invest in external research to evaluate the “efficacy of interventions,” specifically with research looking at how alleged disinformation can be countered and how quickly messages spread. Geoff Hale, the director of the Election Security Initiative at CISA, recommended the use of third-party information-sharing nonprofits as a “clearing house for information to avoid the appearance of government propaganda.”

https://www.nytimes.com/2020/11/24/science/artificial-intelligence-ai-gpt3.html
As if the noise-to-signal ratio of internet content wasn't bad enough.
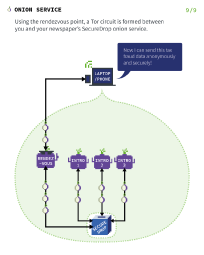
On Hidden Services Staying In The Tor Network
I heard the claim that hidden services don't leave the Tor network by Doctor Mike Pound ( http://grwp24hodrefzvjjuccrkw3mjq4tzhaaq32amf33dzpmuxe7ilepcmad.onion/watch?v=lVcbq_a5N9I https://redirect.invidious.io/watch?v=lVcbq_a5N9I ) and by speakers on a talk uploaded on The Tor Project's channel ( http://grwp24hodrefzvjjuccrkw3mjq4tzhaaq32amf33dzpmuxe7ilepcmad.onion/watch?v=VmsFxBEN3fc https://redirect.invidious.io/watch?v=VmsFxBEN3fc ) and I do not understand how it is possible, since as far as I understand it, the Tor node immediately before the hidden service must decrypt the data before sending it to the hidden service, making it have the same weakness as a typical exit node. As far as I am aware, a hidden service hides its location with a regular Tor circuit from a rendezvous point and regular Tor circuits leave the Tor network, so surely the network for the hidden service must leave the Tor network as well.
how do you glowproof your PC? Do I need to learn how to set up Gentoo? I feel like I'm being watched every second by glowuyghurs, winglows 10 and hackers. They're mining all my data. They're watching me. How do I stop that? I also feel like if I wanted to transfer my files to another computer they would just embed their viruses into my files and infect the next computer. How do you stop it?

Manually upgraded Liberte Linux is better than Tails OS/Kodachi?
Liberte Linux ( https://dee.su/liberte ) is an ultralight (~210Meg ROM, ~192Meg RAM, x86 Pentium Ⅲ) that has both Tor and i2p, first to have UEFI safe boot and laptop mode tools, which are a requirement for my needs and maybe even yours
Why aren't you a site Chad yet?
I recently opened up my own HTTP page and it's incredibly trivial and easy. I know Luke Smith is a faggot but he has solid advice on starting a web page. Using his tutorial on landchad.net I was able to get the site up and running in about 3 hours. Then in 2 days with some on the cuff learning of basic HTML and CSS I had my own perfectly respectable we space up and running in no time.https://leftychad.net you can also do this and I believe that an ecosystem of interconnected webspaces each self hosted is far superior than the soy model of imageboards implemented by our other peers. Just host your own website and you won't have to deal with faggy mods banning you.

Bunkerchan wojak generator script
I've decided to make my script open source. Enjoy.https://pastebin.com/raw/pajZ4N2x
Edit: This script has been banned on leftypol, hobby, tech, edu, games, gulag and anime. But you can still post with it in this thread, I guess.

nuclear space engines
Russia is building a new spaceship they call Zeus, it's made by Roscosmos and it's a nuclear powered space tug.It uses a regular chemical first-stage booster for going to orbit, but once in space they say it will be very fast and out run anything using chemical thrusters. Apparently Russia never stopped working on space reactors, and they do seem to be on track for meeting their timeline to get this thing operational in 2030. It's apparently meant to out-compete Spacex starship in interplanetary travel in speed and cost. It's not a direct nuclear propulsion it's a nuclear reactor powering a plasma thruster, so it's less hardcore than direct nuclear propulsion like an Orion-drive but it's also more realistic that it will actually take flight.
Does anybody know how well this will work ?
Reasons why to use TempleOS
1. Saint Terry made it alone, not outside help except from God's2. made specifically for you, while being universal
3. easy to learn language (like all you've gotta do to say "Hello World" is Print("Hello World); and you're done)
4. very smoll, at 16.5mb of space, better than any linux or windows
5. Linux is a truck with 20 gears to do something simple, Windows is a regular family SUV while TempleOS is a motorcycle, if you lean too much to the left or to the right, you crash
6. No CIA glow uyghurs put their hands on this masterpiece
7. CLI for da B0$$

XMPP server
There's a new Jabber/XMPP server in town, running on Prosody (https://prosody.im).prolesphere.one | d7dchu2gnb4xce7y7vwmulonr4k2wh2dmobqyitwwjeiojfotrvw37yd.onion
Registrations are open, and so is room creation. The MUC (Multi-User Chat) server is at hive.prolesphere.one
The server supports OMEMO and OTR encryption. Expect some growing pains in the early stages, there might be kinks to iron out so server may restart spontaneously. You can report any problems here in the thread or by messaging me at [email protected] (not an email).
You can find a list of XMPP clients here: https://xmpp.org/software/clients/
I use Gajim on desktop and Conversations (available from F-Droid) on mobile.

iToddlers are revolting
Will this lead to anything?https://www.washingtonpost.com/technology/2021/05/27/apple-iphone-monopoly/

Let's talk VPNs
I was using riseup.net as a VPN, but, now cloudflair (The upstream provider for the site) is blocking it. Furthermore, it's come to my attention that riseup boofed their canary after the FBI requested server logs. They are glowin the darks, for real, and confirmed.What VPN would you suggest anon? What VPN, if any, do you use. I was thinking of routing all my traffic over tor, but, currently the site still blocks tor traffic.
Help me out guys, I feel naked, thanks.

Havana syndrome attack info
Looking for details in what's being used for Havana syndrome attacks and will pay Bitcoin. At least .1 btc for anything with proof up front and even more for really good info. Email me with your wallet, info and proof for easy transaction. [email protected]
DarkPaste
DarkPaste - Share Text and Files Anonymously on the Tor Network.URL: http://darkpastendsixpmwpwhfoqlkab74rhopzk26pnca7aapjwr3b5nzgid.onion/trending
Included is a full user system and commenting on pastes. Sticky pastes are possible. Password protection is optional.

I say it’s time we seized the means of crypto production!
https://alexandraocasiocoin.wordpress.com/
Contract Address : 0xd0F2Fc1Ef7d017FB6E1d57d179DD653f5C51311B
<Over 50 holders and counting,
<Liquidity has been locked
<Ownership has been renounced
Come on, guys, let’s get AOC to the moon! sieze yourself a few thousand of the PEOPLE’s coin.

How does refined sand become music?
Does it mimic music? Does it play a worse version of it?How does sound travel from the instruments into a recorder and then a PC?
I am half scared to say that the digimon and real life technology make the same amount of sense to me
I am befuddled when I think about technology materialism, I literally don't understand how 1010010101 becomes something else?
Is the PC tricking my brain to make it think it is something?

Fusion afterburner ?
A nuclear salt water rocket works similar to chemical rockets except it uses nuclear reactions instead of chemical reactions. here is a video https://www.youtube.com/watch?v=cvZjhWE-3zM for the uninitiated. It is the most plausible propulsion system we could build in the near future that is really powerful.It is much better than a regular rocket, it can go up to 1% the speed of light in a few days. But fusion reactions can get you up to 15% light speed, and at that speed you can reach the nearest star system in about 30 years.
So is it possible to modify the salt water rocket to inject heavy-water pellets into the fission plume to get secondary fusion reactions.

How to set up linux for tor usage.
I posted this in another thread but I think it deserves its own thread.I've been seeing a lot of people saying that installing tor is super hard and difficult, and, even if you use windows it's not that hard. All you have to do is install the tor browser and go into the browser bundle files and run the executable for tor, or, just use the browser bundle.Like it's not hard at all.But, being the pros (and dirty commies that we are) we don't use fucking bourgeois Microsoft.So, I've set up a super simple and comprehensive guide to installing and using tor like a pro on Linux.This is why we use Linux.STEP ONE:Downloading tor:ctrl+alt+t: Open terminal:Sudo apt install torsudo service tor startSTEP TWO:Downloading and setting up privoxy.sudo apt install privoxyEdit the config file:vim /etc/privoxy/config(If you don't have vim sudo apt install vim)add in text at the bottom:(vim insert mode: press I)forward-socks5 .onion 127.0.0.1 9050(press escape)Type :wq (write quite)Done, ammo loaded cannons ready to fire.STEP THREE:Set up firefox to use tor:about:preferences: Network settings, Use custom proxy(Privoxy runs on port 8118) 127.0.0.1 8118Check off "Use this proxy for all protocols"Done.Takes literally 5 seconds and you don't have to inconvenience yourself by downloading a whole brand new fucking browser ONLY for the simple task of bouncing around encrypted packets through a bunch of proxies. You also don't have to live with the hellscape that is Microsoft and the billions of exploits and bugs in and written for it. (Not to mention back doors.)And before anyone starts bitching; Setting up firefox for privacy isn't that difficult.Basically turn off all telemetry and geo location, referer headers (but you will need http refer headers for 8chan) and some other shit, Guide here:https://www.privateinternetaccess.com/blog/2018/09/firefox-hardening-guide/But honestly none of that even matters unless you are a windows user or a pedophile and let's hope you aren't either one of those.Have a nice day.
how to fix cheating in FPS games
I know this is firstworldproblemsI don't game so this is really just a commentary from a outsider looking in, but i've recently heard that first person video game developers are thinking about using the TPM (trusted platform module) chip on the motherboard for anti-cheat, this seems like an extreme measure for video games, which got me curious about the problem.
Apparently cheating in video games has become really serious business and very technically sophisticated. Some people even use a secondary computer to run cheat software that generates fake user input signals for a simulated mouse, keyboard and or gamepads. Which means people pay big money for hacks.
Why are game devs trying to beat cheaters in a technical arms-race, instead of trying to make money off of them ?
Cheating doesn't really matter as long as cheaters and non-cheaters don't mix. Because "the experience™" matters.
To fix this, a detailed skill measuring system is needed that is really effective at matching players. The goal at this point is not to detect cheaters, but to indirectly move them to cheater arenas where they can have software robotwars. To make this work you have to do more than just give players a skill rank, you have to generate like a "data-rich" play pattern and match players according to their play patterns. This would probably also fix other issues that diminish "the experience™"
The next step is to develop your own cheat programs and sell them, that way you know who the cheaters are (at least some of them) and you can safely quarantine them in the cheater corner. To get maximum capitalistic cheater-bucks, periodically depreciate the cheat programs. (I know this is really atrocious anti consumer behavior but nobody cares about it in this specific instance).The technical experience you gather from making the cheat programs translates into making good bot-players that you can dynamically remove or add to online matches to balance out mismatched human players.
This hole problem might just be capitalism's fault because how many cheat programs would really be developed in an economy based on production for use rather than production for sale. However it is still plausible that such abuse cases could occur in socialism as well, and i think we ought to find ways to negate the abuse in a more elegant way that doesn't involve punching the donkey. Is there a way to get hack-devs interested in using their skills for a better end ?

Seizing the Means of Anonymous Discussion
Recent events have once again highlighted the necessity of a truly communal, self-governed anonymous discussion forum. This thread is for the development of new forms of decentralized anonymous image boards.The problem in need of a solution is this: [b]How can we develop a forum that genuinely empowers its community and allows them to resist censorship?[/b]
One recent attempt is NNTPChan/Overchan. NNTPChan is a decentralized imageboard that uses the NNTP protocol (network-news transfer protocol) to synchronize content between many different servers. It utilizes cryptographically-signed posts to perform optional/opt-in decentralized moderation. I'm still rather confused on how moderation works there myself.
This seems like a great idea, by distributing a forum across a collection of servers one can resist the disruption of any single server. When 8ch was shutdown by its DDoS provider, however, its community didn't find the motivation to learn from this and migrate to a censorship-resistance platform. Instead its subcommunities were scattered to the winds, the ones that survived coalescing back on a number of individual websites using the classical top-down server-owner structure, with all the authority and alienation from its userbase that it necessarily contains. What lessons can be learned from this? Is there more that can be done?

mega drive
Is anybody willing to speculate whether the mega drive reaction-less space drive pans out ?here is another video
https://www.youtube.com/watch?v=0bp8fk5rosI
the theory part might be plausible

blackICE
ITT post a tool or tools you find useful when attacking, maintaining access, bug hunting, recon or whatever else. I'll start:Weevely3 is my favourite out of the box PHP/.htaccess web shell. Its payload is very small and you can sneak it in to many places and has many features that make the job faster, especially with its pivoting functionality
and lastly its modular allowing easy creation and sharing of new functionality such as adding privilege escalation methods and automated further backdoor and persistent access creation.
https://github.com/epinna/weevely3

NOSCRIPT
This guy wrote an interesting article on using popular sites with javascript disabled:https://www.smashingmagazine.com/2018/05/using-the-web-with-javascript-turned-off/
His experience was that news sites/blogs tended to "mostly" work while most other sites were utterly broken.
WHAT IS /TECH/'S OPINION ON JAVASCRIPT?
I know many on the channers totally disable js in the browser since Stallman wrote an article against javascript many years ago, additionally many are paranoid about browser zero days used by glow in the darks. Finally a ton of people just see javascript heavy sites as being bloated and overengineered, having slow load times and discriminating against minimalism and third world users with slower internet.
With more and more sites using SPA frameworks like vue, react, and angular, and less and less apps doing server side HTML rendering, javascript-disablers are quickly becoming a tiny minority.
What do we think about js vs nojs/noscript?
Federated chans
hi /tech/ , have you seen the federated chans that are coming along?https://fchan.xyz is 4chan + ActivityPub. It's a bit rough around the edges, but it's going to be able to connect to other ActivityPub projects like Lemmy and Mastodon later.
https://0chan.vip is a tag-based textboard that will soon gain a scraper. It also has user-managed boards with stickies, permasage, and a "soft delete" that hides threads in board view, but doesn't delete them from the server. see http://0chan.vip/b/meta/
NNTPchan was kind of cool but it was pretty busted. It fizzled out after a year.

Debian release party
Debian 11 (Bullseye) will be released this Saturday 2021-08-14 12:00 UTCLet's celebrate!
https://lists.debian.org/debian-devel-announce/2021/07/msg00003.html
https://wiki.debian.org/ReleasePartyBullseye
https://www.debian.org/releases/bullseye/amd64/release-notes.en.pdf

steamboy a boon for linux ?
A short while ago Valve announced and demoed a functional gaming handheld, that uses a AMD labtop CPU with a very powerfull iGPU and a beefed up memory-bus for about 500 money.The big wow was that it was running Arch Linux as operating system under the hood, with access to a desktop mode, that would actually be usable as a PC. Most of the people (including me) in the Free Software and Linux scene were excited about this because it means more people using Linux and maybe better driver support.
I have only ever used steam once and i managed to buy a game and then somehow invalidate my license key or user account that was attached to it. I'm pretty sure this was user-error, but still i felt like i was being punished for legally buying a game. I kinda gave up on gaming, although i do sometimes still follow technical news about video game engines.
My experience with DRM systems in general is that it's a fickle bitch and proprietary software doesn't just mean that it's violating the 4 User Freedoms bequeathed to us by Saint Stalllman, it also means that it's probably going to stop working at some point. At least in my case I managed to wrench quite a number of DRMed programs i payed for. I basically think that Intellectual property enforcement is some kind of political, ideological or religious terror, that can only be explained by an unreasonable amount of evilness. I know this sounds a little silly but consider that it feels like unpredictable unexplainable punishment when drm wigs out. Stallman really can feel like a angel descending from the sky telling you a transcendental truth. (Figuratively speaking)
And here is where my doubts come about, steam uses DRM for most of it's games, and Linux users in general really don't like DRM, or proprietary software, and there might be a lot of friction, about it. However I don't think Valve will switch to windows, because Microsoft has it's own videogame-store on windows as well as their own console that is the arch nemesis of Valve and steam. Their dependence on Microsoft is an existential risk and they need something like the steamdeck that is independent of MS to survive as a company. But i fear that there will only be a honeymoon period after which Linux ends up as a battered wife.
I was re-considering my game-abstinence and getting a steamboy, because it looks like you could use it while lying on a sofa and there are a number of puzzel games like the ones from Zachtronics that do look very tempting. However i would immediately wipe the steamdeck and install generic Arch Linux, followed by getting the games from GOG because i hear these aren't cursed by the digital inquisition. I'm probably not the only one thinking about doing this. Valve must have razor thin margins on the steamboy hardware and if a lot of people gog out or use it to sail to a certain bay. They might be induced to wreck the potential for good this might have by trying to rape Linux with a drm sub system and or locking down the hardware.
Microsoft probably will not let Valve get its independence without a fight either, and there might be collateral damage raining down on linux from this.
Now that i managed to make my self feel bad about something i initially felt very good about, i don't actually know anything concrete about any of the active actors involved in this. I secretly hope somebody who does, can prove to me that this will have a happy end and the result will be a genuine linux device that normies like and use, which would reduce the relative precarity of free software somehow.

The shovel
The shovel is a simple tool used to dig various substancesYou can use a shovel to dig farmland, roads, tunnels, holes, mines, foundations, or digging away unwanted substances like chemical waste and mud
A shovels ability to dig however is restricted by the density of the blade, a light plastic shovel will be able to dig conserdiably less than a heavier steel shovel, remember the denser the blade the more you can dig as the mass of the force struck towards the earth when digging overcomes the mass of the ground within a designated area.
Simulating a planned economy
Any programmers here? I thought about simulating a population organizing resources for a while. Nothing serious, just doing it for fun. Anyone tried that before in their free time? Do you have any conceptual starting points? I will start:Type: Person
Attributes: sex, age_range
That is to predict how much resources they themselves need and how much work they can produce. All based on averages.
Type: Resource
Attributes: quantity, state
Subtypes: metal, mineral, wood, food
The attribute "state" describes for example if the resource has been refined based on some procedure. The mentioned subtypes have further subtypes of course.
Type: Product
Attribute: kcal, components
Subtypes: electronics, furniture, dish
kcal is supposed to represent the average amount of work exerted with the most efficient available tools available to produce the product.

Technical idealism
Here is a video from a nice youtube channel that combines entertainment with education.https://www.youtube.com/watch?v=0f9GpMWdvWI
If you didn't watch, it explains the potential for using the heat storage capacity of houses to buffer energy for reducing peak loads on the grid and for buffering renewable energy fluctuations. This can be achieved by using networked devices like the so called smart thermostats that dynamically time shift energy consumption from heating and cooling in the home to low-power-demand periods of the day like late into the night.
It's a very efficient scheme, but reality will look very different. Technical optimization of this type produce a value add which could be used for the benefit of the end user like the video describes it, but that value add is going to be captured by capitalists instead. They will use any of these efficiency gains to reduce their investment-cost in fixed capital like power-transmission-lines and generators. They will not do stuff like improve the grid capacity, they will maximize switching off low income users as long as the existing capacity is enough to not inconvenience all the rich people that will pay higher rates. It will create a divide in society for the ability to use energy.
But minimizing cost and maximizing profitability at the expense of end users is not the only abuse vector. It allows for energy use profiling, which causes all sorts of privacy violations. These will have consequences like the power company being able to find out about your "inflexible power demands" where you will pay the higher electricity price no matter what. Do you like to brew hot caffeinated been juice in the morning ?, well get ready to have your addiction monetized!
This system also gives Capitalists the ability to influence demand. Capitalists do not want to sell commodities for low prices with low profit margins they want to sell for high prices with high profit margins. So what will capitalists do with the ability to control electricity demand, they will remotely switch on stuff until demand causes the prices for electricity to reach the highest level the market will bare. If they can control your heater or cooler they will crank it up to eleven during a demand-troth. If they can they will switch on the heater and the AC at the same time so you don't notice a temperature difference, but if you only have a heater they will settle for turning your home into a sauna. Profit comes before your comfort, what are you going to do not use electricity ?
If you are a friend you will agree that the temperature setting in my house is for me, not for profits, and blame the capitalists who fail to upgrade capacity for power-blackouts.
But lets say we overthrow capitalism, and replace it with a sane economic system where end users can capture the value add, would it be reasonable to do this ? I think the answer to this is still no. We build all the technological infrastructure so we can remove our self from the unpleasant aspects of our environment. And this is reintroducing environmental factors back into the system whose primary purpose is to remove them. Houses are for people, they can be used as a thermal battery, but maybe they shouldn't. We could add dedicated thermal batteries to houses so people don't have to live inside the battery. That way optimizations just can't contradict anybodies comfort, by design.

Getting private data
Hi!I need some real user data, namely - URLs, timestamps and some extra information about the visit. User must behave normally, so typical "pay Turks 1$ and ask them to do actions you need" does not work.
Where can I get such data? As far as I understand, botnet owners might help collecting that. Where can I rent a botnet?

Why is lib culture infesting Free Software (or rather, open source) so god damn much?
Contributor Covenant, RMS cancelling, master -> main, it just keeps on going. It seems like everywhere I talk about software that isn't here or 4cuck, 70% of people hold these retarded liberal views. Why is this and what can be done about it?

Legacy Computer Build
Hello tech! Recently I have been feeling a bit nostalgic as of late and I am looking to build a computer with the best specs I can put in it that will still be reasonable and run windows 98 for nostalgia and classic computer gaming purposes. The only issue I am having trouble with is where, exactly, to start. I was around during this time, but, I was not exactly very tech savvy. I am curious if anyone would have any ideas for how this build should go. What case should I use? Hard drive? Floppy drive? Etc etc.Would enjoy to get this off the ground. I think it would be a neat project. If you have any advice let me know. Thanks, tech.
E-Reader appreciation thread
I love my electronic reader, I must have read hundreds of books on it, all free thanks to the pirate comrades and websites like library genesis, mobilism or archive.org.Picrel is a Kobo Aura with Plato as OS. I hear KOreader is also good.
So fellow anons, do you live fully in the current year? Do you own an e-reader? Do you love it? Are you still hesitating to get one?
Post especially cool websites. Not necessarily sites with cool content.
https://solar.lowtechmagazine.com/ - Website runs on solar power in Barcelona, optimized for low energy use. Has some good articles and a nice 'about' page.

Distributed imageboard software.
Does there exists distributed imageboard software in a sense that each user is a full node? Something like each node running a local server that user can access through browser with local servers synchronizing through DHT or something? All I found is some "overchan" but there is almost no info and as I understand this is not a full-node distributed system.It has been on my mind for quite a long time - Anons need to seize the means of shitposts production.

DeGoogle | How to Escape Google Maps?
I am trying to degoogle as much as possible, but I have yet to find an alternative for Google Maps. I tried some alternatives, but they all are just inferior products with crappier destination times. I live in a huge metro area and—thanks to American-style urban "planning"—I need a good maps application to get anywhere. Can /leftypol/ help me out?Also, general DeGoogle thread.

Free programming languages tutorial
Youtube playlist by a college professor:https://www.youtube.com/playlist?list=PL75YXG7TYNRKHzVmFT2Lh34hMNZ44idSv
videos teaching programming language theories mostly SCALA, with a few bits of scheme/c/js thrown in

Ideal Social network
what would be the ideal social network site???Imageboards (ex: 4chan, *chan “alt chans”):
Pros:
• Anonymous
• No registration
• OP requiring attachment forces content/memes to be produced
• Pruning catalog keeps server space needed to minimum
• Lack of upvote system reduces groupthink and disincentivizes non-originality
• Anonymity + siloing by board centered board identity over personality
• Linear reply structure that requires minimal interaction to read
• Effortposts that do happen are often phenomenal quality
Cons:
• Attracts schizos, racists and “free speech” people who have been banned from other SM for good reason
• Dated UX/UI (mid 2000s approx.) loved by users but retro looking and unappealing to “normies”.
• Dumb curation based on last bump time, incentivizing bait posting (probably this problem shared with other SM)
• Effortposts rare and disincentivized
Notes: Imageboards are in theory fantastic as the fact that they have a limit (usually around 350 threads per board) reduces hosting costs, and also incentivizes people to make interesting posts, because posts that do not garner replies will quickly sink and “fall off” aka get pruned from the catalog. This is also likely what gives chans their edgy character as a “provocative” or edgy post will be more likely to garner the replies needed to keep the thread near the top of the catalog. This can be a problem for quality as a well thought out long form “blog” style post may garner less responses and be far more effort than a 1-2 line “bait” post with an intentionally bad or controversial opinion. In this sense “trolling” and “baiting” are nearly built into the incentive structure of imageboards by definition. Some imageboards try to combat this by imposing a minimum character count for new threads (ex: 200 characters) but this seems like a bit of a hack and is contrary to the overall logic of the medium. Many of the “cons” of imageboards are pros in the eyes of long time users, such as its dated, non mobile friendly UI, and edginess, are seen as needed to preserve the status of imageboard users as outsiders. This creates a unique and culturally prolific space but at the same time dooms imageboards’ mainstream appeal.
Facebook:
Pros:
• Algorithmic timeline microtargets content to users, increasing engagement.
• Social connections keep people tied to platform.
• Makes a ton of money
Cons:
• Reveals personal information about name, job, location, gender, personal relationships status, friends, family etc.
• Incredibly personality centric
Facebook’s business model is pretty simple. Get people to sign up with their personal information and connect with friends (and maybe someone attractive you briefly met at a house party). Then take that detailed personal information and use it to microtarget advertisements at exactly the right demographic for advertisers and political campaigns. Mark Zuckerberg does not believe in privacy. Before facebook, people mainly used screennames and aliases online. It was facebook that changed this, so that people used their real names and faces online. Which is what he considers one of his big accomplishments. Needless to say, I hated this development and I’ve hated the culture it created ever since. Zuckerberg says he made the world more “open and connected”. Another way of saying that is more surveilled and more bothered by busybodies. Anonymity is freedom. There’s a reason every year young people leave small towns across this land to move to big cities, because living in a place where everyone is in your business all the time and a bunch of gossiping people is a prison-lite environment. In a small town, even if you change, evolve, and become a totally different person, people will still remember and think about the things you did as a teenager or when you were twelve. I hate facebook because he’s turned the whole world into one big small town, from which there is no escape. People say the internet is making the world a smaller place, but has anyone ever stopped to ask if its getting too small? But yes, it does make a lot of money. And all they had to do was ruin the internet and possibly break politics to do it. Probably the only thing facebook does well is the algorithmic timeline which increases engagement.
Twitter:
Pros:
• Mobile friendly design
• Decent discoverability
• Hashtags
• Decent editor UI for posting
• Diverse OP content (images, animated gifs, videos)
• Pseudo-anonymity, except for blue checkmarks
Cons:
• Personality centric
• Meme ideologies
• Character limit incentivizes un nuanced “hot takes”
• Forced mobile style UI on desktop (“mobile first”)
• Nonlinear reply structure confusing, forced clickthrough
• Quote Replies
• Notifications mechanic incentivizes performative takes for subs/likes
Notes: Marginally better than twitter but still bad. Character limit makes sense from a mobile first perspective, after all who’s trying to read a 20,000 word thesis on a smartphone screen, however has the side effect of making people reduce their takes to the shortest, most un nuanced, un supported version of itself, which in effect reduces takes to “X bad, Y good” or sarcastic or cryptic one liners. Trump was a master of twitter due to his brain being small enough that his thoughts only require 240 characters anyway. Workaround is creating a twitter thread which is less readable than unbroken text and looks bad anyway, plus people have been trained by the platform to only read short takes and will tune out essay length twitter threads anyway due to twitter induced ADD. Non linear tree style reply structure is confusing and requires too much clicking to read through. The positive thing is the infinite scroll provides a constant stream of content, if the person limits their interaction to scrolling and liking only (not replying or reading replies). Editor for posts is far superior to any non facebook platform. Quote retweet allow “dunking” and incentivize leaching off original content, “reply guys” who quote tweet someone else and add their own vapid or sarcastic commentary. Read somewhere that the twitter engineer that invented the quote retweet regrets it (as he should). Even regular retweeting is pretty lazy. If the only purpose of retweeting is outsourcing discoverability to the user, a better mechanism is needed. While imageboards incentivize creating content that gets a lot of replies, twitter incentivizes getting lots of likes, in fact a high reply to like ratio is considered a bad thing “getting ratio’d” as a reply with no like is a proxy for dislike. So while imageboards do not distinguish between positive and negative interaction, twitter and all other like based systems implicitly encourage “performative” content creation/takes a.k.a users saying the things that they think other people will like, to therefore increase their own visibility, celebrity, etc. Rather than saying their honest opinion, if indeed they have any. Exporting Los Angeles style “trying to become famous” culture to the rest of the world. This is a cancerous dynamic. Should avoid like/dislike systems at all costs, esp. as complex feelings are reduced to a binary attribute (like/dislike). Possible side effect = polarization?.
Reddit:
Pros:
• Pseudo-anonymity
• Communities based on interest not personality
• Generally medium to medium-high quality content
Cons:
• Post History visible reduces anonymity
• Branching reply structure
• Terrible UI
• OP too short (as a “link aggregator” its often just a link to a news article)
• Likes/Dislikes, Karma, Gold, Silver, and the rest of that bullshit
Notes: Reddit is a website with a decent concept but a bad UI and worse userbase. Yes, as a channer the typical image of a “redditor” comes to mind. A limp dick neckbeard soyboy with a rick and morty t-shirt. Reddit is the Thomas Edison of websites, its users steal all their content from people that actually make original content, repost it, and then act like they invented the whole thing. A perfect encapsulation of middle class bland yuppie suburban consumer culture, a circlejerk which produces nothing original and never will. Part of the broader disneyfication and pg-13ification of a sterile and desexed pop culture, with a good dose of smarmy smarter than thou smugness and milquetoast center-left politics thrown on top. Peak midwit. Certain subreddits are niche and good. Reddit evolved to replace a lot of the old school bulletin board forums for niche gaming/auto/etc interests. At least its based on shared interests and not personality based drama. Like/Dislike and karma system encourages the same hivemind and performative posting BS as with twitter. At worst as a “link aggregator” it simply acts as a comment system for articles on websites that don’t have their own comment section. Not much to be borrowed here mechanically, except maybe allowing users to make a http link as their op as an alternative to videos/images.
Blogs:
Pros:
• Pseudonymous option
• Potentially very high quality content
• High word count
Cons:
• Low discoverability
• Bad on mobile
Notes: Blogs and blog-like sites like Tumblr are actually surprisingly good. Unlike the transient nature of twitter posts, people tend to put effort into blogposts and even include sources from time to time. The only problem is that blogs tend to be separate websites and even when on the same domain (ex: wordpress.com) they tend to lack discoverability. Tumblr at its peak in the early 2010s seemed like a transitional website, a sort of nu-myspace. The downside of high character count is that blogs, regardless of “responsive” design, tend to read badly on phones and don’t lend themselves well to casual use.
Tiktok:
Pros:
• Extremely potent mandatory recommender system driven content
• Short video clips lend well to casual use
• Video format more accessible to dimwits and tired people than walls of text
Cons:
• Often cancer tier ultranormie content, on par with instagram
• Primarily consumed by children and teens
Notes: Tiktok’s content may be cancer but it’s format is genius. The most addicting app of the modern era. Instead of allowing people to search for content but adding recommender systems like youtube, tiktok leans in and puts it on steroids by making the recommender system the main way to access content. This is like increasing the nicotine content 3x.
Youtube
Pros:
• Audiovisual and audio content easier to digest
• AV/A content easier to listen to while moving (i.e. commuting or walking)
• Works for both long and short content
• Recommender Algorithm very good
Cons
• Video storage takes a ton of space on disk.
• Streaming content in a timely manner tricky, practically mandates CDN use
• Responses text-only
Notes: The second most popular social media network. Takes way too much storage for video. On the plus side the recommendation engine is scarily good and addictive. AV content can be consumed with walking, driving, etc. while reading text for that is pretty difficult. Object storage and delivery (files, videos, images) is a usually overlooked aspect of these sites. Responses being text only is listed as a con, but it can be a pro in the sense that it saves storage space and it encourages being OP-centric in an r9k-ish way.
Runner ups:
Linkedin – facebook for jobseekers, professionals, and hustle culture psychopaths.
Snapchat – fancy texts that delete themselves.
Pinterest – Not familiar enough to comment but looks like a glorified booru for middle aged women
Telegram/Signal/Whatsapp/etc. - Texting that’s ““secure””.
Medium – Blogging for people who are too lazy to set up their own blog. Often mistaken for legitimate “news”.

>corporation threatens to deport man to China and report him for protesting the CCP because he developed a sheet music downloading program that they claim violates their copyrights
What's your take on this?
https://github.com/Xmader/musescore-downloader/issues/5
https://archive.is/qmPFa

Is there any good streaming services?
Does anyone know of any none fucked streaming services? Particularly ones that aren't shit on android? Youtube is trash for a whole host of reasons, especially on mobile. I'm not paying for spotify ever and doing anything on there just assaults you with an infinite amount of adds. Choose something — adds, rewind something — adds, don't skip a song in days — adds. I've always liked pandora and always thought it's a great idea but the execution is rather flawed. It seems to only play new or rarer stuff once in a blue moon. So does anyone know of any non-shit tier streaming?
Future of Chinese made CPUs
Since US tech embargo on China is still in effect and US plans to squeeze Chinese tech companies by restricting their access to computer chips. China's reaction to this was to make one of their goals to have a home-grown alternative for Intel, AMD, TSMC and the like to decrease dependence on the US. So I was wondering what kind of progress have they been making lately and what are their prospects of ever having a viable alternative to Intel and AMD?There is all this talk about SMIC, Loongson and Zhaoxin and that in early 2020 Zhaoxin allegedly published a chip comparable to 2017 level intel and AMD tech and they are planning to have parity with Intel in a few years. Then there are Some sources are saying that China is failing horribly at acquiring manufacturing tech for more advanced processors. And I really can't make any real sense out of it.
So when will I be able to buy a computer that uses a hardware that dunks on burger made tech and sends my personal data to Beijing instead of Washington, if ever?

Email Providers
So based on basic Opsec I've been reading about you should have a seperation of your identity from your logins on TOR and whatnot for reddit or twitter or whatever the fuck. But all that shit requires emails and all these damn email providers require a phone number which defeats the whole purpose? Which email service can I use that won't demand my phone number and let me stay as anonymous as possible online?
Windows 11
What the hell is this garbage? I thought it was a practical joke for a solid 5 minutes before realizing that it's actually real. It looks like a GNOME knockoff. Thoughts?https://www.youtube.com/watch?v=GFW27oG9gs8
https://en.wikipedia.org/wiki/Windows_11

I am sending books to my kindle via email. Amazon then asks for confirmation. I obviously haven't paid for those mobis. I wonder if they will eventually knock the door and say I own them all the hundreds of books I might have sent.
I really wonder how copyright laws work especially in the age where everything is datamined. The probably know every single porn I may have downloaded too.

I hate how "pozzed" the internet has become
I was logging all network traffic and noticed requests to googleusercontent at seemingly random times and also to Amazon's AWS. Now I'm worried what it could be sending/receiving.All I could find was a couple of stackoverflow questions about the same thing saying it was apparently NetworkManager (thanks, GNOME!) but I don't have it installed.

Disruption of Boston Dynamics Digidogs/Police Drone "dogs"
Hello lads, I'm looking to start a conversation on a topic that's been popping up alot recently, and will likely develop further as the technology gains more adoption. As I'm sure you know, robotic dogs from the likes of Boston Dynamics are being rolled out at police departments and military bureaus across the US, and I'd bet we see widescale adoption as the technology is fleshed out further.So as a result, I'd like to start a conversation on the best feasible means, both expensive and DIY, to deal with these fuckers. With the advent of home-based 3D printing, easily accessible lasers, and other modern user tech, I believe there are a number of options available to us.
In the resistance against drones being used by the police in Chile, Argentina and now in Portland, lasers were used to incapacitate drone dogs during protests. However, this incapacitation *only* makes these dogs unusable at that single protest; any police department will simply repair their $75k digidog and send it back at the next protest. So, what I'm interested in is ways to make them *inoperable* for extended periods of time, whether physically or electronically. I was bouncing around the idea of somehow using very strong magnets to damage the internal electronics, but this may be unfeasible due to the size of magnet that would be needed. Other options that seem viable would be permanently damaging the optics being used by the dogs, but I'm not sure on the best option for this. As such, I'd like to open this to conversation. I'll be posting this thread here, as well as on a few other imageboards that may be interested and able to help in this discussion.

Porky needs "Diversity in Tech" to slash salaries in IT
I was listening to a Citations Needed episode about the propaganda trope of "Labor shortages" and realized that all that WE NEED MORE WOMEN AND PEOPLE OF COLOR is not about making software companies less monocultural (which is good in itself), and the real porky's goals are:1. Increasing the overall supply of engineers, like they pushed women into the workforce in the 60s in the West.
2. Getting the candidates who tend to accept lower salaries (at least women are routinely underpaid, probably PoC too).
In fact, CN hosts briefly mentioned it themselves:
> what they want to do is they want to expand the pool by any means necessary, whether they use liberal inclusion language or whether or not they use, they want to have more workers because if I have twenty people applying for a job versus three, the demands, of course, will be far less
https://citationsneeded.medium.com/episode-135-the-labor-shortage-ruse-how-capital-invents-staffing-crises-to-bust-unions-and-fb42448a7e23
Somehow, the whole inclusivity hype should be hijacked with unionizing, because who would oppose the white'n'male CEOs' tyranny if not a diverse labor movement?

Fediverse general
Does /tech/ participate in the Fediverse? Seems to me that this is the sort of social media we should be trying to get people into, even if social media itself is kinda trash.I've always disliked social media, but after the news at >>>/leftypol/1066439, I've been considering getting into the Fediverse. You see, I would like the people who DO use social media (basically everyone) to be on better platforms, but I feel I cannot demand that from them if I cannot even use them myself. For instance, it would be disingenuous to ask Comrade Cockshott to start his presence in Mastodon after getting banned from fedbook if I could not be there to follow him and boost his follower stats. So..
So, /tech/, any thoughts on the Fediverse? What are some good instances and communities I could join? What are some people I should be following? What implementations are better, Pleroma, Mastodon, something else?
Also fediverse general.

Microchan Project
Hey /tech/ I've been working on a chan with a relatively modern UI/UX as a side project. I thought about adding this to an existing thread but didn't want to shit them up.I have several goals:
1. Modern UX/UI - I wanted to give the chan/imageboard a modern makeover using modern HTML/CSS, yes, with rounded buttons etc.
2. Code Quality - I'm not a nazi about code quality on hobby projects like imageboards, but imposing some sort of basic framework or structure would still be a vast improvement over vichan style imageboards which are mostly structureless spaghetti code balls. Statically typed languages also help with this.
3. Spam Filtering - some sort of pre-emptive validation or spam filter, possibly using basic classifier algorithm, to help moderate the board.
Things that are done:
- Basic posting (threads, replies)
- Catalog View
- Support for images (jpeg, png ,etc.)
- Catalog Pruning (delete last threads on catalog after X threads)
- Links (double carrot style links to other posts and OP)
- Greentexting
- Orangetexting
- Redtexting
- Embedded Youtube Links
Things that aren't done yet:
- Non Catalog/standard view (still needs work on pagination)
- Support for videos and pdfs
- CSRF
- Moderator and Admin tools/menus & UI
- Spam Filtering
- Front/Home page with metrics
- Overboard
- Show replies to post near top of post (double carrot links to posts that have replied to that one)
- Floating Reply box in thread
- Reporting
Reach Goals:
- Themes/custom css
Things I'm probably not going to do:
- (You)'s/(me)'s
- Hiding Posts/Threads

SPA vs Server Side
Are javascript/typscript based single page applications better, or server side template based rendering? Do we really need something like react/angular?I know /g/entoofags hate javascript because stallman told them to like 10 years ago but normalfags will complain if their front end experience isn't silky smooth with js animations and shit
Obviously some applications like darknet markets try to minimize or eliminate the use of javascript for security reasons.
server side html rendering also makes app deployment simpler since you don't have to worry about the front end and back end separately.
OTOH separating the front from the backend helps make a richer UI and also separation of concerns. Also makes it easier to swap out UIs
What does everyone think?

Oh god
oh fuck
I'm retarded.
I've never been tech-savvy, just a pleb consoomer and user, never digging deeper than what was on surface level.
But it seems to be, based on what I've been hearing for the past two years, that those who don't have a workable knowledge of it will simply be considered the illiterate of the 21st century.
What bare bones basic, and I'm talking like Primary School shit I'm just that dense, level stuff should I learn?
So far I've got:
- Linux (no fucking clue how I'm going to learn it)
- Python (seems accessible and is used in some GAN AIs which I find interesting, so kinda motivating)
- Ruby (it's easier Python, is it really worth it then?)
- C++ (I've just seen it everywhere I have no idea what it actually is)
- Java (always thought it was only for free online games)
- The Pragmatic Programmer, and that other one that's blue and has weird symbols and like old medieval manuscript people on the front.
- I have a 3D printer, and access to Scratch and some kid's programming software.
Honestly, I'm not wanting it to be a career, I just don't want to get fucked by glowies and would like to know that I can at least "write my own name/ABCs" etc.

Audacity may collect "Data necessary for law enforcement, litigation and authorities’ requests (if any)" according to new privacy notice:
https://www.audacityteam.org/about/desktop-privacy-notice/

Fucking Scams
How do we fight back against the crypto-tards? They currently have a monopoly on credibility at the moment and I'm fucking tired of it. With the increasing escalation of tech censorship over the last several years we have ourselves a golden opportunity to grow the communities of censorship-resistant decentralized federations, and the crypto scammers keep managing to siphon people off into their unsustainable pyramid schemes. Every time their spokespersons get thrown a softball interview and every time they seem completely incapable of articulating and justifying their system because, gosh, it's just too darn complicated for the average person to understand! And it seems like nobody is paying any fucking attention when this happens routinely because blockchain and electronic tulip bulbs are some magical mysterious technology that you have to do a doctoral dissertation to understand, but just trust us it works. How do we fight back against the anti-intellectualism of crypto woo?
Help me develop a text board for gemini
Hello, tech, I'm looking to develop a leftypol textboard for the gemini protocol. I am curious about where I should get started, or, what language would be optimal for this. I also don't really understand how to get one language to interact with another language. (Gem text and Perl for example) I don't really want to do anything huge or something that will blow up I am just a hobbyist looking to do something fun and interesting. thoughts?
Nice, now I have to carry my fucking phone around with me every time I want to check my fucking work emails because some prick at IT decided to force everyone on to two-factor authentication in order to interact with the mail server. So much for choosing to opt out of mass surveillance and the socially-malignant perpetual connectedness of carrying a phone everywhere. So much for email being convenient.
It disgusted me when Google and other Silicon Valley monopolies started forcing 2FA on people because I see it as little more than an excuse to coerce people into giving up contact information to better track and surveil them. What's the real deal with two-factor authentication? Why is it seemingly impossible to find an article critical towards it on a simple web search?
Wrote stuff about fires use it for whatever you like
brief observations on fires>1:Once a substance is ignited it cant be set on fire again
>2:fires spread based off their temperature, the hotter a region is the faster the fire spreads
>3:Objects will increase in mass after being set on fire
>4:an unbreathable smell will be created after an object is set on fire
>5: fires are observed to die when covered with something with alot of mass even if it is flammable
hypothesis
>1a: the reason why you cant set a burnt object on fire again is because the substance has already reacted with its environment in a matter that it cant produce an exothermic reaction again
>evidence: when I put an ignited match in water 5 times the fire on the match went out 100% of the time and couldnt be ignited again
>2a: fires spread in volume based of their temperature
>3a: fires form when a substance,combines with oxygen(or another substance that triggers an exothermic reaction) and begins to break down and release massive amounts of energy towards its surroundings in the form of heat, when this happens a chemical reaction occurs and thus the ignited substance reacts with the substances around it to form compounds thus forming substances with heavier masses than the substance before set on fire
>4a: a human being cant smell anything other than oxygen contentrated in nitrogen meaning when a substance becomes ignited it forms an unbreathable substance naturally through a reaction
>5a: thats simply a biproduct of resistance towards a force, if an object with alot of mass overcomes a force it simply will not move, likewise if a fire tries to cause an object to react its temperature needs to be high enough that the molecules surrounding the fire create a force strong enough to generate a reaction otherwise no reaction occurs, summarized: a fires temperature and mass will determine how much resistance it may overcome in order to ignite its surroundings, hotter and heavier fires can burn more flammable things, smaller and cooler fires cannot
<ideas on fires
>A fires rate of expansion(expansion distance per second) is based off the force of attraction between molecules that trigger the exothermic reaction that causes a fire to form
>fires naturally diffuse and spread faster and faster as there surface area increases over time and the amount of substances becomes accessible to the flame again increases over time
>how much a fire can burn is based off how much energy the fire can utilise to do the work required to trigger reactions
>condensed flames are hotter and can burn more flammable objects because molecules within the igniter(the source of the fire) have less space to diffuse and likewise collide with each other more rapidly leading to increased amounts of pressure and therefor force at the expense of size

linux failure
Does the failure of Linux desktop prove that communism will never work?feels like a barely functioning toy compare to the commercial options. they argue over irrelevant differences, constantly reinvent the wheel, never innovate, barely handles the basics.
it has no profit motive to unite or to sort boring problems.

Secure/anonymous laptop
I want to get an old thinkpad, like an x200 and make it into a secure, tor-only machine. What is the best way to do this? Something like Qubes OS or is that just a meme? Looking for solutions for full disc encryption, network card that connects to TOR alone, that kind of stuff.Thanks.

Holy shit, Google and Apple may have unwittingly just destroyed the highly unethical false-sense-of-security marketing of encrypted-messaging apps to dissidents and whatnot.
For years, many of us here on /g/ who have 200+ IQs and who keep our computer gear in a basement Faraday cage alongside our anti-psychotic medication have been alerting the masses that you can't have a secure encrypted-messaging app on an endpoint device that's Swiss cheese. We've been talking about exotic baseband attacks, OTA SIM attacks, 0days against software running on the AP, etc.
But if the latest reports about auto-installed COVID apps in some states are true and not Qoomer-tier nonsense, Google and Apple are perfectly happy to give governments the keys to the kingdom for installing whatever the fuck they wish on a device. Poof go any assurances that dissidents have with regard to their encrypted-messaging apps.
Keep an eye on this. Shit is about to get lit in the neurodiverse community.

Languages
What programming languages do you guys use? I'm mostly Python, Java, C#, C++. Used to like functional programming but IMO now that regular OO languages have alot of function features like first class functions its not as big a deal to write code in a pure functional language like lisp or haskell, better to write regular python or something and occasionally write some functional-styled code
How does anyone use the APP? I have tried to use that app over and over again and i just can't get adjusted to it.
This isn't a knock on the devs or the hard work they have done or the people who use it. It has done a lot of good and with out the app we very well wpuld have probably been put on a different time line where the forces pf evil and the bunker won out.
That being said, I just don't get it. Aesthetically the app is very jagged and rough on my eyes. When in comparison to just the normal browser view I still get to pick my themes and the themes look like they do on my desktop machine. There's also just the general browsing experience. The browser allows me to judt browse the board as if i was on my desktop, but, the app just feels counter intuitive to the browsing habits of imageboards i have acquired over the years.
Can some one explain to me?

/tech/ Matrix chat - SICP study group
Hello there, /tech/ comrades.I am passing by to let you know that a Matrix chat for /tech/ talk has been created! The chat has been added to the official leftypol community. This chat is meant to serve as a place to talk tech and programming in general.
Come join us! The link is: https://matrix.to/#/#leftylambda:matrix.org?via=matrix.org
This chat will also be hosting an SICP /read/ing group. That is, we will be studying the book "Structure and Interpretation of Computer Programs" and helping each other solve the exercises. For those unaware, SICP used to be the introductory textbook for Computer Science classes at MIT back in the day, and remains a cult classic to this day. It can be used as a general introduction to programming, but will also be rewarding for those more experienced.

All AMD Processors Since Phenom II Have BadBIOS Circuitry That Leaks to the Military
Title gives my conclusion from empirical events I witnessed and inside info. PSP runs on the same circuit, but isn't the backdoor per se, which has been around for much longer.Just like AMD was able to change the crypto algorithms for the Zen chip they licensed to China, they can change how the CPU behaves at any system, even those already deployed. This can be used to sabotage any program or computation, making BadBIOS (uses radio, not sound) vastly nastier than StuxNet.
American military made a grave mistake by giving access to the morons of the Brazilian military, who are letting knowledge of this spread like a fire (and misusing it for petty profit and inside jobs to justify a police state). Israel, UK and France also have access, but are much more professional.

Anybody else following the current Freenode drama/exodus?
Yet another example of our projects failing. The internet as a liberatory force has been an abject failure.
You love to see it.
https://www.kline.sh/
https://fuchsnet.ch/freenode-resign-letter.txt
https://web.archive.org/web/20210514121343/https://p.haavard.me/407
https://gist.github.com/joepie91/df80d8d36cd9d1bde46ba018af497409
http://techrights.org/2021/05/13/private-internet-access-and-freenode/
https://coevoet.fr/freenode.html
https://gist.github.com/aaronmdjones/1a9a93ded5b7d162c3f58bdd66b8f491
https://gist.github.com/jesopo/45a3e9cdbe517dc55e6058eb43b00ed9
https://blog.bofh.it/debian/id_461
https://meta.wikimedia.org/wiki/Wikimedia_Forum#Freenode_(IRC)

>Firefox is owned by the Mozilla Corporation.
>The so-called Mozilla Foundation is the parent but Firefox is part of a taxable for-profit entity.
>Further, Mitchell Baker seems to be the CEO of, guess which one, BOTH. Unbelievable.
>>In 2018 she received a total of $2,458,350 in compensation from Mozilla, which represents a 400% payrise since 2008.[14]On the same period, Firefox marketshare was down 85%. When asked about her salary she stated "I learned that my pay was about an 80% discount to market. Meaning that competitive roles elsewhere were paying about 5 times as much. That's too big a discount to ask people and their families to commit to."[15]
>>By 2020 her salary had risen to over $3 million, while in the same year the Mozilla Corporation had to lay off approximately 250 employees due to shrinking revenues. Baker blamed this on the Coronavirus pandemic.[16]
From https://boards.4channel.org/g/thread/82064105#p82066677

A Mystery Malware Stole 26 Million Passwords From Windows PCs
>Researchers have discovered yet another massive trove of sensitive data, a dizzying 1.2 TB database containing login credentials, browser cookies, autofill data, and payment information extracted by malware that has yet to be identified.>The stash also included over 1 million images and more than 650,000 Word and PDF files. Additionally, the malware made a screenshot after it infected the computer and took a picture using the device’s webcam. Stolen data also came from apps for messaging, email, gaming, and file-sharing. The data was extracted between 2018 and 2020 from more than 3 million PCs.
https://www.wired.com/story/mystery-malware-stole-26-million-passwords-from-windows-computers/
Yet another data breach happened.

Privacy general
Comrades, we need a thread on privacy. Any decent activist should try ways of staying anonymous on the web and prevent being tracked by governments and corporations.General tips===* Use free software as much as you can.* Use GNU/Linux and keep it up-to-date, to be sure that you don't have unpatched security exploits* Don't use Flash Player, use youtube-dl instead for watching streaming videos online* Do not use Google, use DuckDuckGo or StartPage instead* Use a password manager like Keepass or for GNU/Linux users keepassx. Create new passwords for every site that you visit and use a strong password as a master password. A tip for easy remembering of your master password is to use a sentence. "i fucking love cookies and tits!" with extra capital characters etc. is easier to remember than some random characters and long enough to prevent brute force attacks of any kind.* Use the Tor Browser Bundle if you really want to stay anonymous.Firefox====* Go to Preferences -> History and set History to "Never remember history". * See for additional tweaks: https://github.com/amq/firefox-debloat and https://vikingvpn.com/cybersecurity-wiki/browser-security/guide-hardening-mozilla-firefox-for-privacy-and-securityAdd-ons-----------* Use uBlock Origin for preventing tracking etc. Bonus: use hard-mode to manually whitelist external domains on sites. Don't use uBlock but be sure to use uBlock Origin https://github.com/gorhill/uBlock/wiki/Blocking-mode:-hard-mode* HTTPS Everywhere* DecentralEyes: prevents CDN hosting from tracking you (Google for Jquery etc.)* Self Destructing Cookies: only allow cookies that you choose to allowOS==* Encrypt your hard drive or home partition at least* If you use GNU/Linux, you can try to restrict systemd or syslog from logging. * Use a distribution which takes security seriously. Also, be sure that you don't install a lot of things outside the repository. It will cover most of your needs.Real life tips===* Pay with cash if you canFeel free to provide tips to each other comrades!
Japanese AI reconstructs thoughts based on brain activity
>“We have been studying methods to reconstruct or recreate an image a person is seeing just by looking at the person’s brain activity,” Kamitani, one of the scientists, tells CNBC Make It(…)“These neural networks or AI model can be used as a proxy for the hierarchical structure of the human brain,” Kamitani says.>While the idea of computers reading your brain may sound positively Jetson-esque, the Japanese researchers aren’t alone in their futuristic work to connect the brain with computing power.
https://www.cnbc.com/2018/01/08/japanese-scientists-use-artificial-intelligence-to-decode-thoughts.html
Within some years privacy will be an outdated concept.

Linus swearing at antivaxxer
He's back.https://lore.kernel.org/ksummit/CAHk-=wiB6FJknDC5PMfpkg4gZrbSuC3d391VyReM4Wb0+JYXXA@mail.gmail.com/

Electrical Engineering / Learning Hardware
I'm looking for recommendations on resources, learning materials, or general advice when it comes to learning about electrical engineering. Books, videos, MIT courses, you name it. I'm open to starting with the absolute basics from Physics 101, which I admittedly have not brushed up on in a while.In addition, I'm also interested in tinkering with hardware as part of the learning process, so any advice on that front would be greatly appreciated.

Qubes OS
I use it daily and it's great. It never crashes on me and it's easy to use.The only problem is that it's picky with hardware. You can buy an old thinkpad to run it on and if has an Ivy Bridge CPU, you can disable Intel ME. IMHO disabled ME and Qubes gives you the most secure computer for daily use.
What do you guys think of Qubes?
How do we get around the centralization of the web? It seems like a herculean task. I made my own email server but it took me so long just to be able to make it so that outlook.com accounts could receive them at all. I tried to do it from scratch and it would be received by google (as junk initially) and yahoo (junk initially) but not outlook (failed to receive). So I learned about Mail in a box and screwed around with nameservers on namecheap and it worked finally. But outlook still marks it as spam. A lot of people use outlook.

PROGRAMMERS WANTED: SOCIAL MEDIA APP
https://github.com/ComradOrg/Comrad
https://www.bizjournals.com/kansascity/news/2021/06/03/stealth-data-anonymous-online-traffic-data-mining.html
Chad is going to reveal people's names, job titles and other private information from web traffic. Beware!

Opinions on suckless? I kinda like the concept but the idea of sharing the space and potentially looking for problem solutions together with alt-right retards who unironically rant about "social marxists" makes not wanna use their stuff. I know it's kind of illogical but I get a weird feeling whenever i'm about to git clone their repos or if I'm trying to look at examples and all I get is Luke Smith's videos about it.

Wearable technology
I think it's moronic and doesn't have much practicality but might be used in a better way in a communist societyWhat do you think about wearables and do you think it would exist in an advanced socialist society?
https://youtu.be/ud6uNY5E2wQ?list=TLPQMzEwNTIwMjFsed4l0KCO_A
Just look at how stupid this shit is

so /tech/
How would we make https://leftypol.org/leftypol/res/279348.html#279864 happen IRL? What kind of libraries should I be learning to use if I were to implement something like this?
>picture probably unrelated

Hardware Backdoors
Are there any laptops on the market without hardware backdoors like Intel Management Engine or AMD Platform Security Processor? There's a group working on building a Power ISA based laptop (since IBM made Power ISA open source in 2019.) This is the only modern hardware that I know of without a backdoor, but it's not in production yet. https://www.powerpc-notebook.org/faq/
A half assed summary of computers and CS
Computers are machines that can perform a range of different tasks based of user input. Normally to achieve their main function they are composed of switches whom when turned on will perform a function and not when turned off that are connected through a series of wires connecting to each switch that transport electricity based off what the person wants the machine to turn on and off. We represent on and off states of computers using 1s and 0s.An algorithm is a series of instructions given to a computer that gets it to turn different sectors of itself on and off in a specific sequence.
A cpu is an abbreviation for Central Processing unit, it runs all the commands that allow which sectors of the computer to turn on and off
Software is an app composed of many different algorithms a computer uses to perform a specific set of tasks
Hardware is the components and machinery of the computer itself
Computer science or CS is the study of well computers
Supercomputers are large warehouses of cpus that are often used in performing major projects
Quantum computers are computers that can be in an on and off state and allow any cpu to be much more efficient than in the traditional sense where a computer can only ever be on and off
Ai and machine learning are software based tools used to get computers to perform labour on their own
Robotics integrates complex hardware and software to get different types of machinery to be able to perform complex tasks driven by algorithms and ai
Hope to all the undergraduates in this degree can use this awful post for something
Why the fuck is no one here talking about FreeNode fucking imploding on itself? They are banning whole channels on the network for even mentioning the name "Libera." The glowies got control of freenode, fyi, so, if you are on that network I would suggest leaving.
https://arstechnica.com/gadgets/2021/05/freenode-irc-has-been-taken-over-by-the-crown-prince-of-korea/

So what the fuck is this
https://odysee.com/@OdyseeHelp:b/monetization-tutorial:5
Its a decentralized peertube-like streaming platform. BUT they say they can pay creators in crypto. How? Where is that money coming from without ads? Something doesn't add up

Google tells you what to search now too
>Be me>Use andOTP
>Lose phone
>Want to use 2FA
>None of the solutions on github page for desktop decryption of the json file work
>Search authy
>No use
>Hear about KeepassXC having TOTP stuff
>on top of search bar google says
>"based on your recent search activity you should search for "KeepassXC 2fa"
<mfw it was right
<mfw still can't access my accounts and will need to download a 1gig android emulator to use andOTP apk

China’s Setting up a Hotline for Snitching on Cryptocurrency Miners
China can't stop winning.https://www.tomshardware.com/news/china-establishes-cryptocurrency-mining-hotline

Cryptocointards are going after SSD and HDD now
https://www.storagenewsletter.com/2021/04/27/chia-driving-wild-storage-land-rush/https://www.extremetech.com/computing/322261-crypto-manipulation-is-causing-a-short-term-storage-shortage
https://www.tomshardware.com/news/chia-500-percent-increase-adata-high-capacity-ssd-sales
https://www.techspot.com/news/89489-chia-crypto-mining-spurs-500-jump-adata-ssd.html
https://www.pcworld.com/article/3616700/chia-cryptocurrency-threatens-to-spike-ssd-prices-like-bitcoin-did-to-gpus.html
https://www.thestar.com.my/aseanplus/aseanplus-news/2021/05/02/chinese-coin-miners-flock-to-new-cryptocurrency-chia-resulting-in-hard-drive-shortages-and-price-surges

how do you make a “Cybernetic culture research unit” that doesn’t even know how to use SSL?
what’s with this phenomena of lit majors larping as tech bros?
http://ccru.net/

https://www.baldurbjarnason.com/2021/the-oss-bubble-and-the-blogging-bubble/
< Babel is used by millions, so why are we running out of money?
> This doesn’t surprise me. The purpose of the web software industry is to extract value out of Open-Source Software (OSS). Everything is built under the misconception that OSS is abundant, replaceable, and free.
> People don’t appreciate just how much web dev is about extracting value from OSS, both on individual and corporate levels.
> [..]
> Web development? Everything is built or run directly on OSS.
> Almost everything we do in web development exists as a thin layer over open-source software.
> Servers, build tools, databases, ORMs, auth, client-side JS, web browser: we are all building on a vast ocean of OSS labour without paying back a fraction of the value we generate. It isn’t just big, direct dependencies like Babel that are suffering. The stuff your stuff is using—the infrastructure code everything needs—is surviving on sheer inertia as well.
> That’s value extraction. Strip-mining if you want to hammer home the unsustainability. Looting if you want to emphasise the moral dimension.
Is open-source close to collapse?

functional programming
Functional programming was a craze.I've learned scheme and common lisp and scala and haskell in classes at uni/grad school and although in the 2010s the functional programming craze was huge eventually it died out and people just decided that low level languages like go and rust were better and that even java could be good if you add lambdas and first class functions/function objects to it. I was a full on FP cultist from 2010 to like 1-2 years ago.
After writing actual functioning apps in functional languages I've concluded that old fashioned OOP/java and now low level multi paradigm languages like go are probably better than the languages like clojure or haskell which force functional style and take up huge amounts of memory due to immutable data structures, despite the compiler writers best efforts. The concurrency benefits can simply be gotten by adding a few functional features to mainstream languages which they have already done, for example, C# and Java. Although C# does it way better imo.
I see literally no reason to write an app in haskell, clojure, scala, etc. over basic Java/C# or rust/golang

Buttcoin
I know, you're asking yourself already, how the fuck are crypto's compatible with a leftwing communist image-board? Well, first of all, fuck you, we live under capitalism and as such must exchange and purchase under the current mode of production we find ourselves under.Second, I would like some one to help me understand, exactly, how to set up a bitcoin, monero, what have you; wallet. I tried to set this up on my laptop but syncing with the bitcoin network is a huge MASSIVE bitch and took me months and I never got fully synced. Also, it takes a shitload of resources to work properly on my computer. I can barley do anything else.
So, my question is: What is the best way to get into bitcoin and use bitcoin and other cysto's like a boss? Am I doing something wrong? What are the best specs for btc and the like? As always, any help would be appreciated. Thank you /tech/!

Is OOP a meme?
I am currently going through my first OOP course in Uni and I can't shake of the feel that this is an overhyped meme. Sure, it is very useful in certain cases, say if you are making a video game or some other big project, but it just seems useless for day-to-day coding where you are just trying to execute a specialized instruction. I just don't encounter a situation where I would have that many different type of semi-related objects that it would warrant the use of family hierarchies and etc. Am I just too unexperianced with coding and miss something, or is OOP just not that amazing as its made out to be?
Why is setting this piece of shit up so fucking difficult? Come to think of it? What the fuck are computers so fucking difficult? It seems everything I do on a god damn computer these days breaks something, or, I didn't do it right, or it wasn't the right architecture, or, what ever the fuck man. Seriously, this shit has gotten out of hand. It shouldn't be this god damn hard to have freedom in my own fucking home.

Barron Samedit
https://blog.qualys.com/vulnerabilities-research/2021/01/26/cve-2021-3156-heap-based-buffer-overflow-in-sudo-baron-sameditThis exploit was sexy, implementation was neat. bug was obvious. I am immensely jealous.
What do you guys think about it?

What's this about a Chinese satellite being out of control? Sounds like a dumb hoax.
http://orbit.ing-now.com/3dlaunch/payload/data/2021-035/

Wobbly: an app for 21st century workers’ power.
Wobbly is a workplace organising platform, being designed and prototyped by a small voluntary team of developers. It’s a communication and coordination tool, with structures and processes modelled on the IWW’s organising style (hence the name, coming from the IWW nickname). We’re creating a space for energetic, powerful, and democratic unions to win struggles, grow.https://notesfrombelow.org/article/an-introduction-to-wobbly
https://github.com/Wobbly-App

Searx
I know that if I run my own instance of searx is the most private way to search things up. But what about public instances of searx like search.snopyta.org, are they any safer than just using pure duckduckgo? Because I am still trusting a 3 party with my data, the only other advantage that I see using a public instance of searx is that is completely open source. Are there any other positives?
>write articles about relationship between Oracle and China and mass surveilance
https://theintercept.com/2021/04/22/oracle-digital-china-resellers-brokers-surveillance/
https://theintercept.com/2021/02/18/oracle-china-police-surveillance/
<Oracle VP: If you have any information about Mara or her reporting, write me securely at kglueck AT protonmail.com
https://web.archive.org/web/20210428135055/https://www.oracle.com/news/announcement/blog/the-intercepts-latest-2001-04-27/
lol
digital hygiene
I find myself drawn into obsessively wasting my time on the internet. i used to be more productive when i didnt have a smartphone but now, the itch of having distraction at my fingers every single minute of every day has tanked my attention span and drags my attention away whenever i do work.There has never been better systems of control than these that keep us occupied on vapid bullshit at all times of the day.
i know i can fight it but i need some tools. How do you guys mitigate the itch to look at your phone or whatever. i live in China so i cant get out of using my phone for literally everything, you cant survive here without one on your pocket. But whats your advice/ tools for mitigating this?

FUCK THESE THINGS
I HATE ANTI-DESIGN MAKINGA PHONE SHOULD BE USEABLE WITHOUT NEEDING TO CARRY ACCESORIES FUCK THE HELLSPAWNS THAT CAME UP WITH THIS CRAP
I LOSE THAT LITTLE EJECTOR AND I LITERALLY HAVE TO PAY MORE MONEY TO USE SOMETHING THAT I OWN
WHAT IS THE FUCKING PURPOSE OF THIS SHIT
NOTHING WORKS ON THAT STUPID RETARDED HOLE EVEN
NEEDLES OF ALL SIZES FAIL
I HATE THE MODERN WORLD

>The emerging dream of an internet where every interaction is a financial transaction
https://reallifemag.com/paid-in-full/
I FUCKING HATE TECHBROS Why is this shit presented as a good thing?

/bot/
Discussion of automated bots and scripts.Hello comrade wizards of /tech/ I am making a thread to seek advice regarding the implementation of simple bots and scripts to simulate user actions. Our team has been experimenting with simple bots ran using tamper monkey, and we are looking to learn more. Please share with us your arcane knowledge in the field of bots, scripts, and sock puppets. And use this thread to discuss anything related in general o7

Friendship ended with AGPL. Now SSPL is my favorite copyleft license.
https://en.wikipedia.org/wiki/Server_Side_Public_License

Making free software and keeping it free
Spin off from >>7090Right now we're under threat of big tech companies finding loopholes on the GPL to take out software and make it closed source without giving anything back and because the FSF is staffed by corporate stooges once Stallman dies we're at their mercy.
We also need to promote the use of copyleft licenses and dissuade people from using permissive licenses.
What is there left to do?
Lawmakers call YouTube Kids a ‘wasteland of vapid’ content
https://apnews.com/article/susan-wojcicki-2dd9c3b6f6044950db817c1092a87296Not even wrong.
Exploiting vulnerabilities in Cellebrite UFED and Physical Analyzer from an app's perspective
https://signal.org/blog/cellebrite-vulnerabilities/
MOXIE POST BINARIES OR STFU LIBERAL

Tor hidden services
Know some good shit on Tor? Let us know. Whether it be substitutes for clearnet services, or just the .onion domain for whatever, or just something cool.What I found:
>privacytools.io site
privacy2zbidut4m4jyj3ksdqidzkw3uoip2vhvhbvwxbqux5xy5obyd.onion
>Invidious (YouTube front-end)
http://grwp24hodrefzvjjuccrkw3mjq4tzhaaq32amf33dzpmuxe7ilepcmad.onion/
(Clearnet version: https://vid.puffyan.us/ )
Requires enabling certain scripts to work unfortunately. You can sign up and make a list of subscriptions though.
>Nitter (Twitter front-end)
http://3nzoldnxplag42gqjs23xvghtzf6t6yzssrtytnntc6ppc7xxuoneoad.onion/
>/leftypol/ (/leftypol/)
http://wz6bnwwtwckltvkvji6vvgmjrfspr3lstz66rusvtczhsgvwdcixgbyd.onion/leftypol/catalog.html
Some things I was interested in hearing about:
>email over Tor (with clearnet email compatibility if possible) (I tried Protonmail and it asked me for SMS, Paypal or credit card to continue, kek no thanks + I had to enable scripts + it made me go through a clearnet URL)
>games over Tor (doesn't matter what, just would be a cool novelty)
>social media over Tor (could be chans, larger social media substitutes, etc.)
>whatever other shit you found that was cool